
Avaya IX Messaging is available in a version that is certified JITC compliant.
The Joint Interoperability Test Command (JITC) is a certifying agency for I.T. products for the U.S. Department of Defense. Corporations that deal with the various branches of the U.S. government may be required to have their software JITC certified to maintain the highest levels of interoperability, safety and security. JITC certified software has additional layers to help protect the client than non-certified software products.
Avaya IX Messaging can be purchased in a JITC certified format which encrypts the database files using FIPS approved encryption. Other security sensitive files and folders within Messaging are encrypted using Windows EFS. Communications use encrypted TLS (Transport Layer Security) protocols. This keeps all of your data and communications secure. Please contact your reseller for details.
|
Note: The steps in this chapter only apply to sites that have purchased a JITC license for Avaya IX Messaging. If your site will not use JITC, you can skip this chapter. |
When installing Avaya IX Messaging version 10.5+, almost all choices regarding program configuration are asked at the beginning so that the many components can be installed without interruption. The only variation that occurs after the initial selection is the PBX and integration type, which will be unique to most sites.
|
Warning: The instructions found in this guide cannot be guaranteed to work for all installations since each site is unique. Some problems may arise even if you follow these instructions precisely. Therefore, use this document as a reference for your own configuration, making the changes appropriate to your site's specific requirements. |
|
Requirements |
Details |
|---|---|
|
License |
JITC License for 10.8. |
|
Software |
For details on Messaging 10.8 Hardware and Software requirements please consult the Technical Operating Guidelines. |
|
Important: Microsoft Windows is not provided with any version of IX Messaging. The customer must install and fully update a suitable, licensed version of Windows onto the hardware platform before proceeding with the Avaya IX Messaging software installation. |
|
Note: Avaya IX Messaging has only been validated on Windows in English and in French. Other varieties of Windows may not work as intended. |
|
Note: Avaya IX Messaging should only be installed on a dedicated server specifically intended for the purpose. Sharing system resources with other applications may prevent Messaging from functioning properly. |
|
Caution: It is strongly recommended that the operating system drive has a minimum of 100GB reserved exclusively for the O/S. This is in addition to any amount required for the Messaging voice server installation. |
•A JITC specific license for Avaya IX Messaging must be purchased.
•JITC installations are only supported on Windows Server 2012 R2 (64-bit).
All other system requirements are the same as for any other Messaging installation.
Deployment Configuration Considerations
•An Avaya IX Messaging server may be installed on the root drive (the same drive where Windows is installed). This must be a local drive. iSCSI targets are not supported.
•An Messaging server may be installed on a secondary drive (on a different drive from where Windows is installed). This must be a local drive. iSCSI targets are not supported.
•The drives may each be a physical drive (for best performance), or a single drive with partitions.
•The folders \uc\logs, \uc\DB, and \uc\messages may be mounted to a local drive. Network or mapped drives are not supported.
•In an ESX(i)/VMWare environment, SAN/iSCSI is supported, but only at the ESX(i) level. The iSCSI target must be mounted and managed by the ESX(i) host. If a virtual machine is to have a C drive and a D drive, they must be added as a virtual hard disk using the VMWare client.
•The rules for drive types and options are the same for virtual machine environments. The storage must be local, Direct Attached Storage or SAN.
|
Warning: These configurations have been tested and approved by Avaya for use with Messaging. While other configurations may be possible, Avaya cannot provide support in these areas. |
It is suggested that any antivirus applications currently active on the server computer be disabled during installation. Any other resource intensive applications or monitoring tools which may cause a conflict with the installation should also be disabled during the installation process.
For Microsoft Windows Server 2012 R2, you must ensure that all the necessary server roles and features are installed on the system before proceeding with Messaging installation.
1.From the Server Manager Dashboard, click Add roles and features.

If this screen is hidden, go to View and select Show Welcome Tile.
2.Click Next.
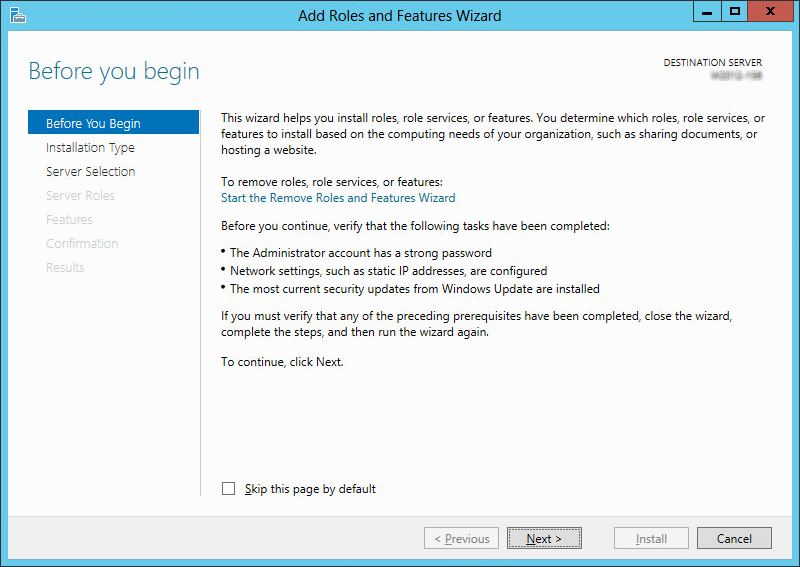
3.Leave the default settings as they are. Click Next.
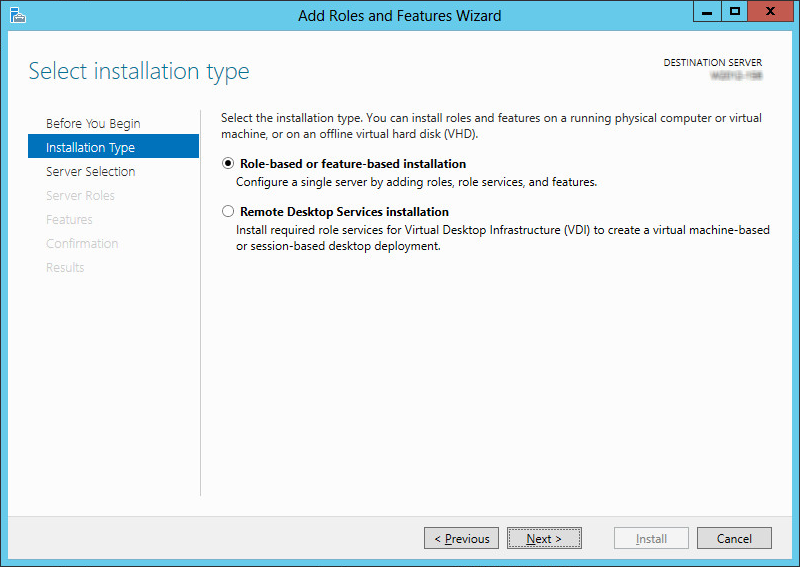
4.Leave the default settings as they are. Click Next.

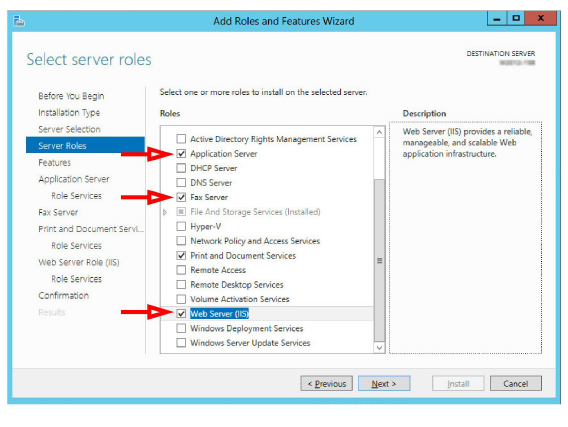
5.Enable the Application Server, Fax Server and Web Server (IIS) checkboxes.
Click Next.
|
Note: Throughout this installation, whenever you are prompted to confirm additions, always select Add Features. 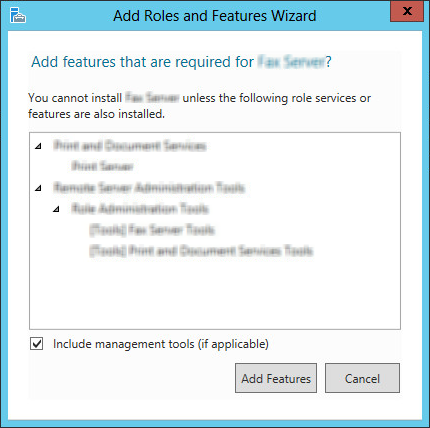
|
6.Enable the .NET Framework 3.5 Features checkbox. Click Next.
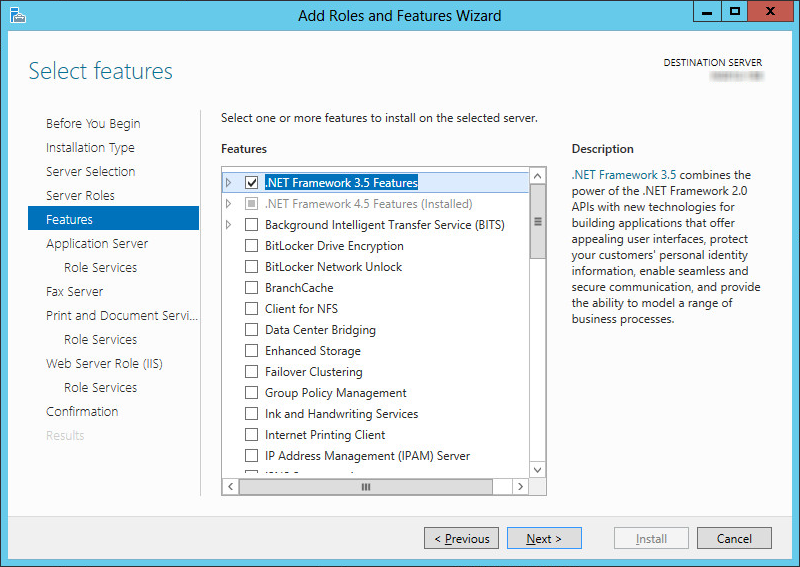
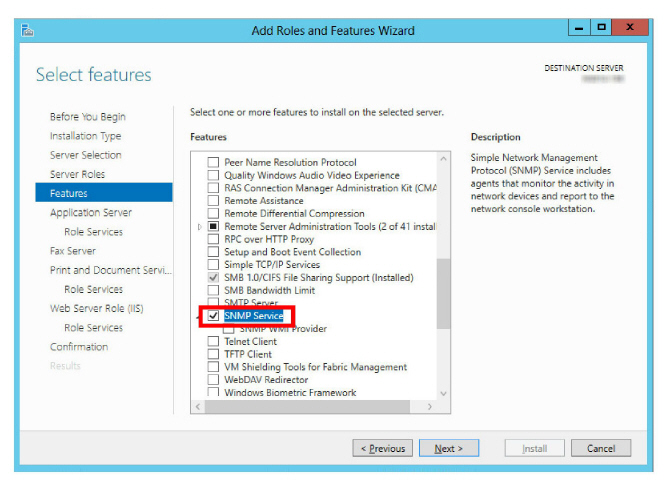
7.Optional: If you plan to use SNMP Alarms with Messaging, the SNMP Service must be added to Windows before the program can be installed.
If SNMP Alarms are required, scroll down and enable SNMP Service.
If SNMP Alarms are not required, skip this step.
8.Review the information, then click Next.
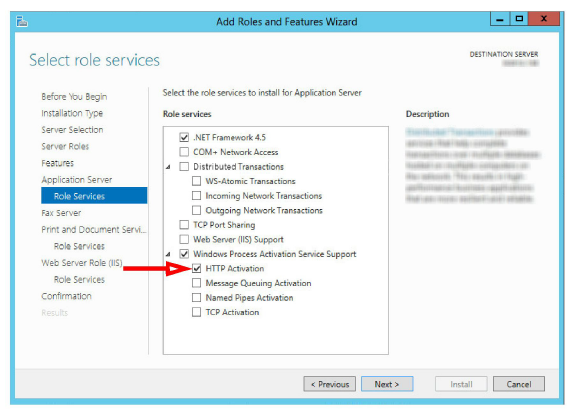
9.Ensure that HTTP Activation, under Windows Process Activation Service Support is enabled. Click Next.
10.On the Fax Server screen, click Next.
11.On the Print and Document Services screen, click Next.
12.No changes are required here. Click Next.
13.On the Web Server Role (IIS) screen, click Next.
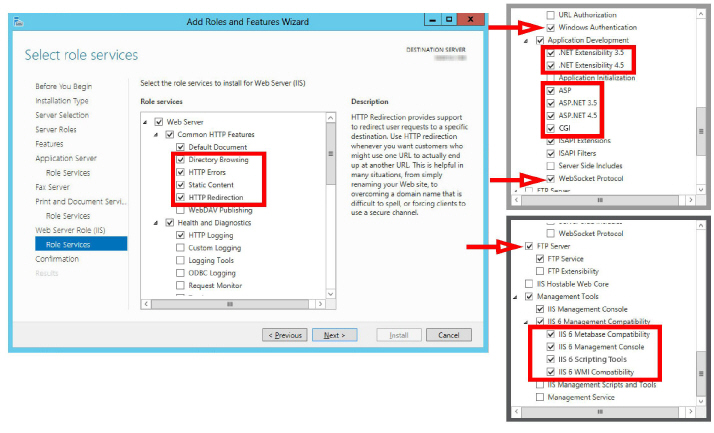
14.Open Web Server > Common HTTP Features. Enable Directory Browsing, HTTP Errors, Static Content and HTTP Redirection.
Scroll down to Security, and enable Windows Authentication.
Under Application Development, enable .NET Extensibility 3.5, .NET Extensibility 4.5, ASP, ASP .NET 3.5, ASP .NET 4.5, CGI and WebSocket Protocol.
Locate FTP Server and enable FTP Service.
Enable all options under Management Tools > IIS 6 Management Compatibility.
Click Next when ready.
15.Review the selections here. When ready to proceed, click Install.
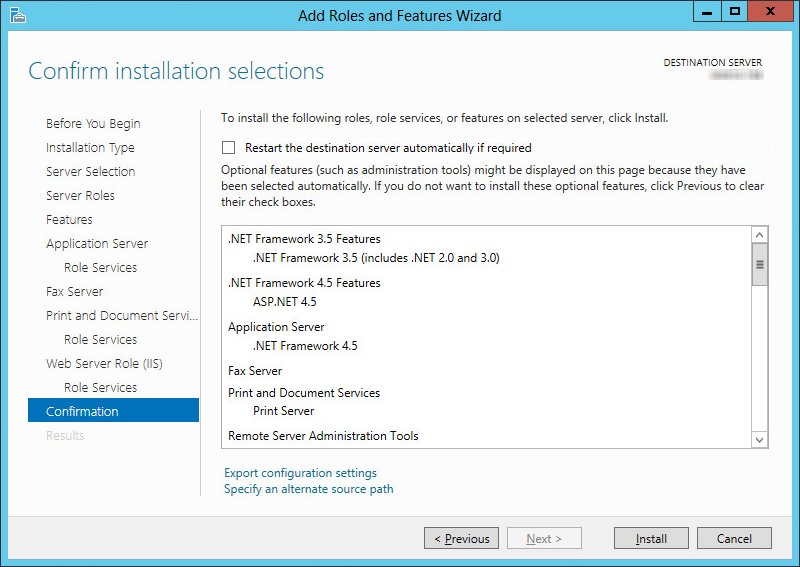
16.If prompted to provide the Windows disk to load the files, click Specify an alternate source path and direct it to the appropriate drive.
|
Hint: This is particularly important for virtual machine installations where there may not be a drive configured locally. |
17.Windows will now start the installation process for the chosen items. This process may take a while.
|
Note: This window can be closed without interrupting the installation procedure |
18.Once all changes are complete, Restart the server.
Installing Microsoft .NET Framework 4.7.2
The Microsoft .NET Framework 4.7.2 is a required Windows component but it cannot be installed as part of the program package. It must be added by the administrator.
The installer can be downloaded from the Microsoft site here:
Follow the instructions provided to install .NET Framework 4.7.2 onto the server.
Installing Certificates for Encrypted File System (EFS)
During installation, Avaya Messaging uses the Windows application Cipher to encrypt security sensitive files and folders. This uses the certificate installed in the Personal folder of the current user (the service/DCOM user created during installation). The certificate includes Encrypting File System under Intended Purposes.
Therefore, to ensure JITC compliance, you must to import the EFS certificate before installation.
Digital certificates can be purchased from a trusted Certificate Authority (CA), such as GoDaddy™ and Symantec™. A properly constructed certificate issued by your corporation’s IT/Security team can also be used.
|
Important: Self-signed certificates are not permitted with JITC installations. |
Installing a CA Signed Certificate
A Certifying Authority can issue a certificate to your company. They will provide a file containing the certificate and the password that opens it.
Save the file to a known location on the voice server hard drive.
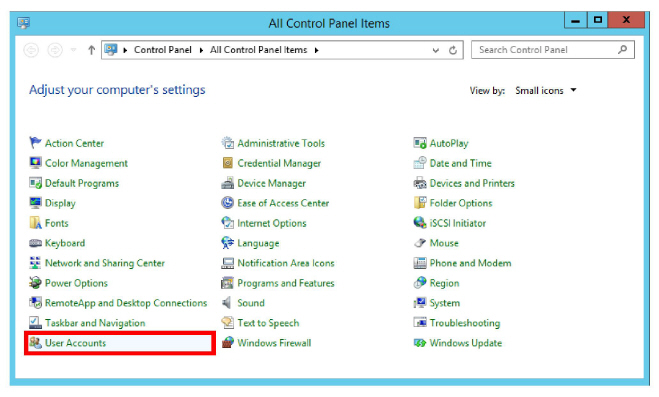
1.Open the Windows Control Panel and select User Accounts.
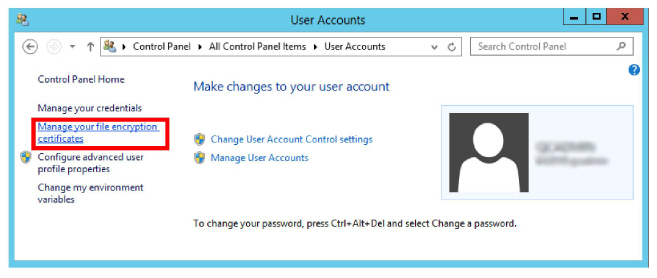
2.Click Manage your file encryption certificates.
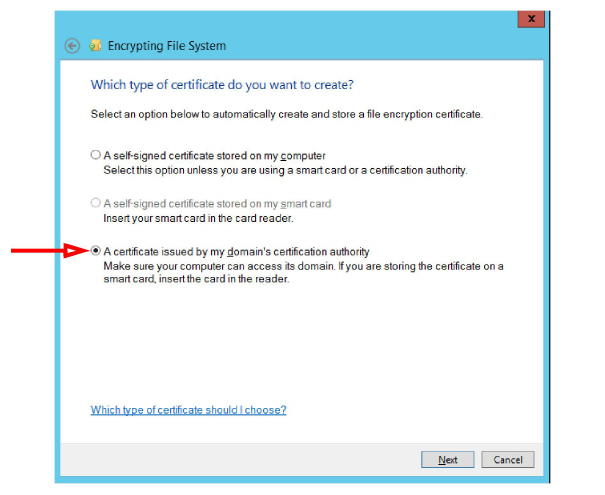
3.Select A certificate issued by my domain’s certification authority. Click Next.
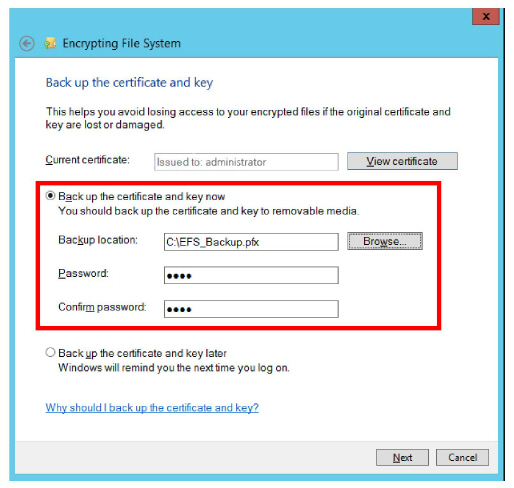
4.Enable Backup the certificate and key now, fill in the path to where the backup file will be saved, and give it a password. Click Next.
|
Important: If you are using a different certificate file, make sure to back it up once installation has finished. Instructions can be found in the Backup and Restore the Certificate File section. |
5.Enable All Logical Drives, then click Next.
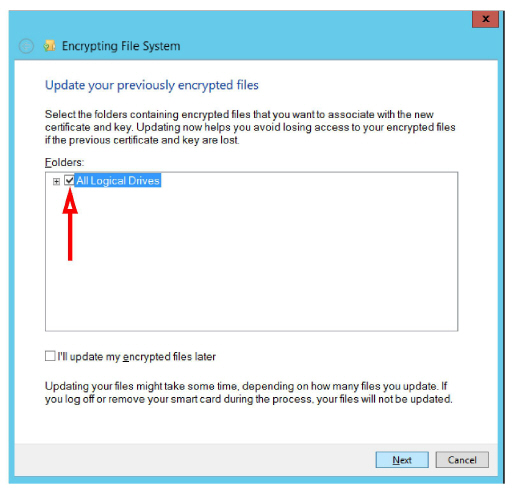
6.The files will be encrypted. When it is finished, a result summary will be displayed. Click Close.
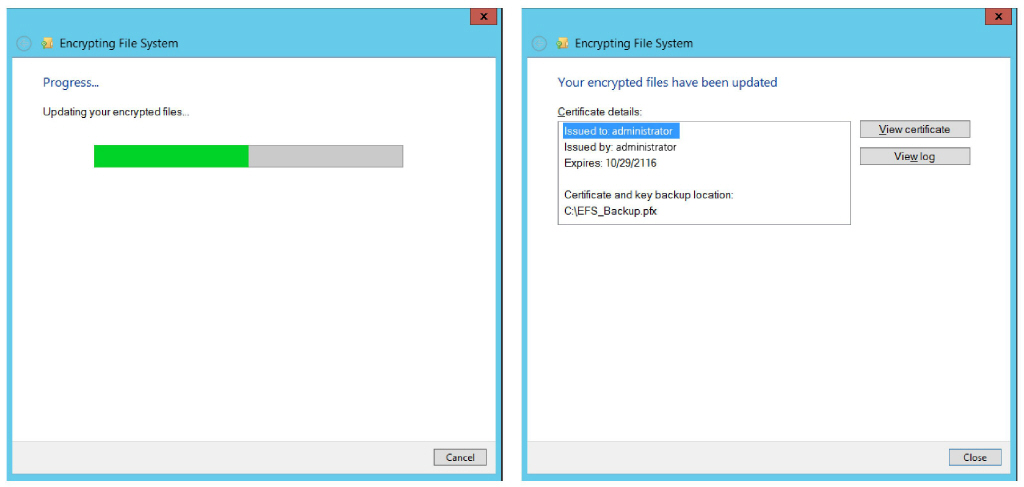
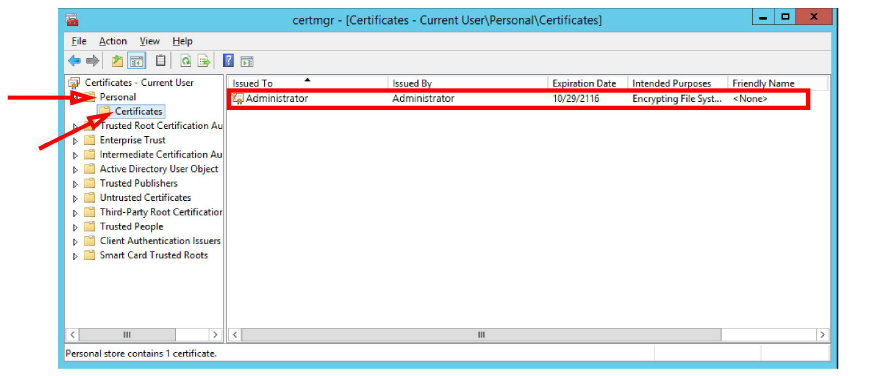
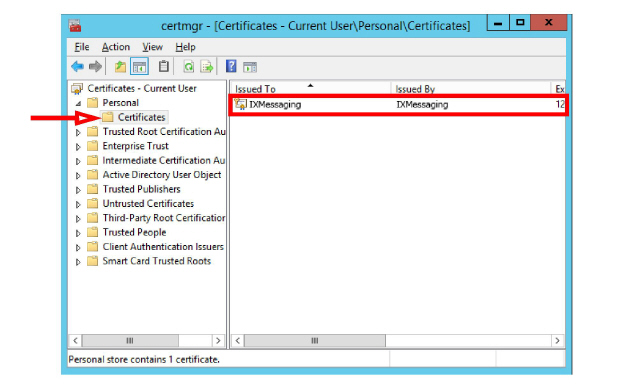
7.You can verify the success of the installation by opening the certmgr.msc.
Go to Personal > Certificates and verify that the certificate appears under your user name.
Backup and Restore the Certificate File
If you are using a certificate file from another source, or if you have not done so already, you should create a backup copy of the file. If the certificate becomes corrupt, none of your data will be accessible unless the certificate can be restored.
This section covers how to backup and restore the certificate file.
To create a backup copy of the certificate file...
1.Launch the Certificate Manager console in Windows.
Right-click the Windows icon and choose Run. Enter certmgr.msc and hit OK.

2.In the left-hand pane, open Personal > Certificates. Your certificate(s) will be displayed in the right-hand pane.
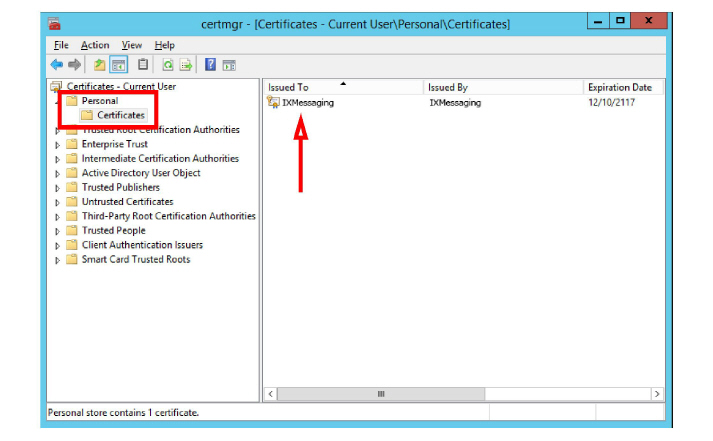
3.Right-click the certificate and select All Tasks > Export.
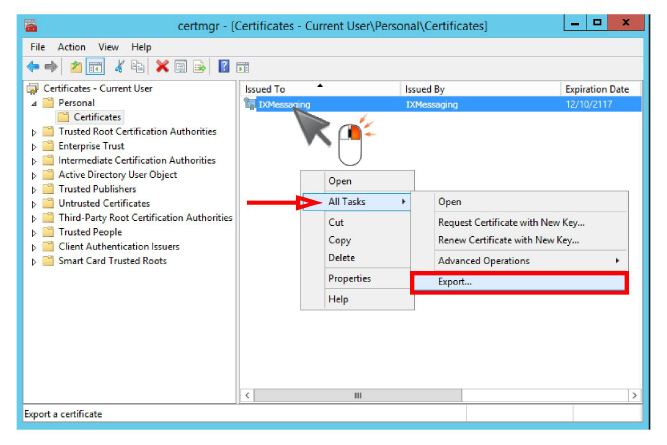
4.When the Certificate Export Wizard starts, click Next.
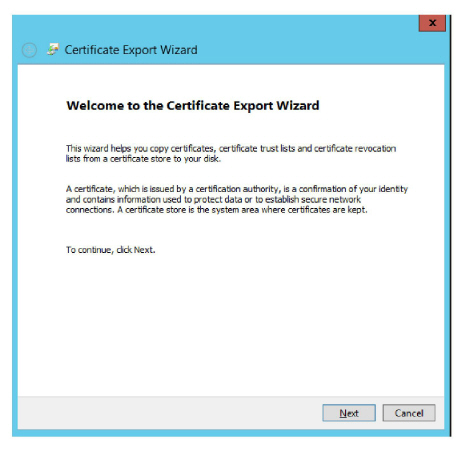
5.Enable Yes, export the private key and click Next.

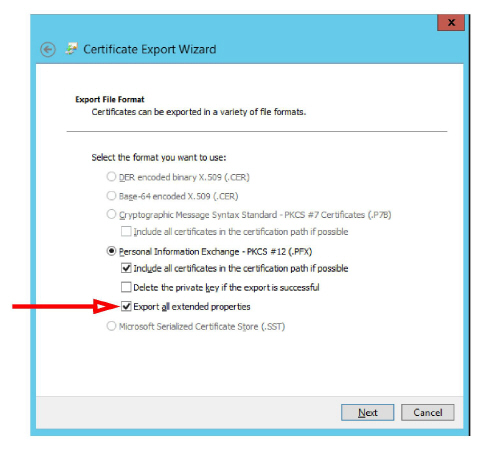
6.Enable Export all extended properties. Choose Next.
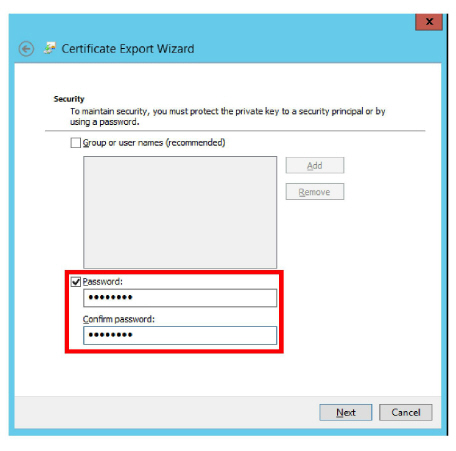
7.The backup copy of the certificate file requires a password for encryption.
Enable Password, then enter a password and re-enter to confirm. When ready, click Next.
|
Important: Record this password and keep it in a safe location. The loss of this password will lead to the complete and unrecoverable loss of data if you ever need to restore the certificate file. |
8.Save the file to your hard drive. Click Next.
9.All parameters have been configured. Review the settings and click Finish when ready.
10.A backup of the certificate file has been successfully created. Click OK.
For maximum security, copy the file you just created to another drive (e.g. on another computer, network storage, on a thumb drive, etc.). If the original computer is completely inaccessible, saving the file to another location will still allow you regain access to the system.
To restore the certificate file from a backup...
1.Launch the Certificate Manager console in Windows. Right-click the Windows icon and choose Run.
Enter certmgr.msc in the space, then hit Enter.
2.In the left-hand pane, the Personal folder will be empty.
Right-click in the right-hand pane. Select All Tasks > Import.
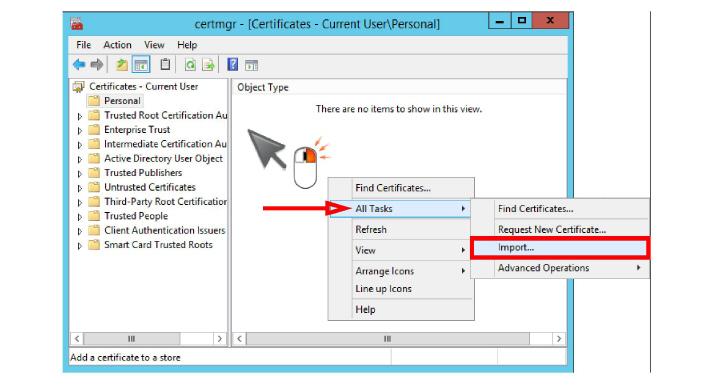
3.When the Certificate Import Wizard starts, click Next.

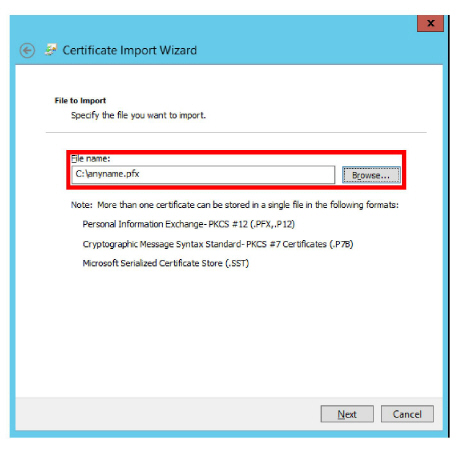
4.Locate the backup file and select Next.
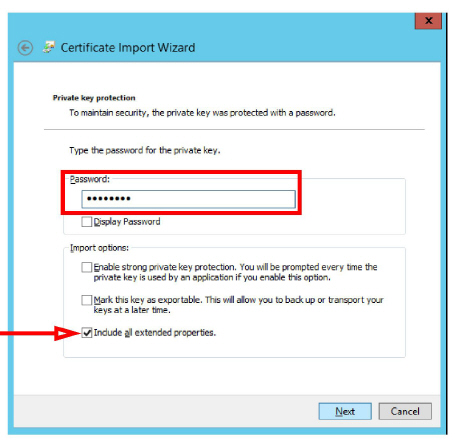
5.Enter the password that was used to secure the backup file. Enable Include all extended properties.
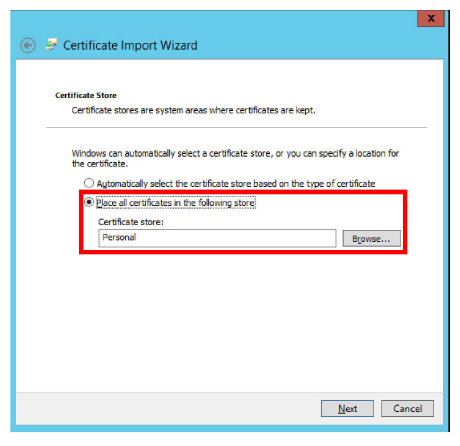
6.Ensure that the restored certificate will be copied to the Personal store and click Next.
7.The configuration is complete. Review the settings and click Finish when ready.
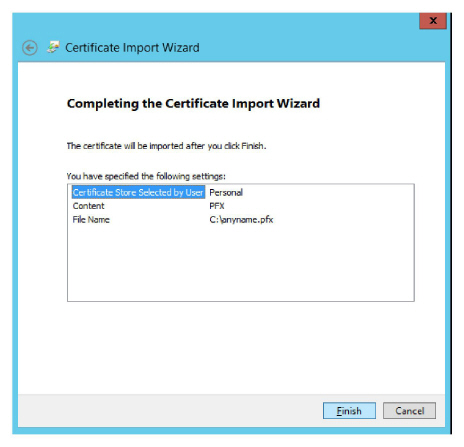
8.The certificate file will be copied onto the operating system of the current computer.
The certificate file has been successfully restored.
Reboot the server to have the changes take effect.
Import the Certificate on All Servers
|
Important: The following procedure must be completed on all servers in a High Availability installation; Primary, Consolidated, and all Secondary servers. |
1.Login to the server as any user.
2.Right-click Start > Run and enter CMD to launch the command line editor.
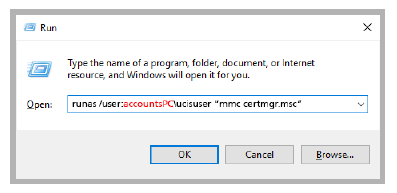
3.At the command line, enter the following inserting your credentials:
runas /user:computername\UciisUser “mmc certmgr.msc”
Click OK.
When prompted at the command line, enter the password for the UCIISUser.
The Certificate Manager console will open.
|
Important: The following command must also be run on the Consolidated server only. runas /user:computername\ucAdminUser “mmc certmgr.msc” |
4.In the left-hand pane, the Personal folder will be empty.
Right-click in the right-hand pane. Select All Tasks > Import.
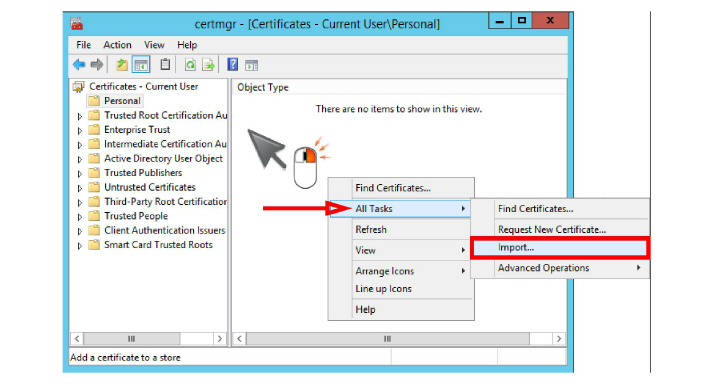
5.When the Certificate Import Wizard starts, click Next.

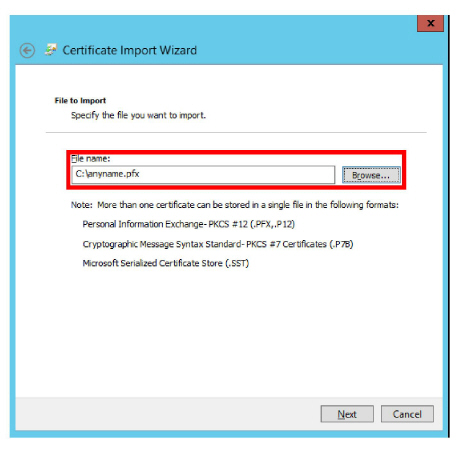
6.Locate the backup file and select Next.
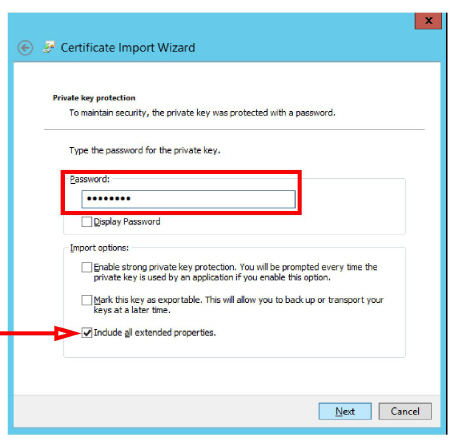
7.Enter the password that was used to secure the backup file. Enable Include all extended properties.
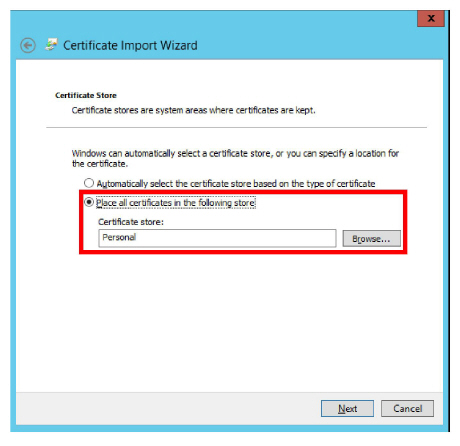
8.Ensure that the restored certificate will be copied to the Personal store and click Next.
9.The configuration is complete. Review the settings and click Finish when ready.
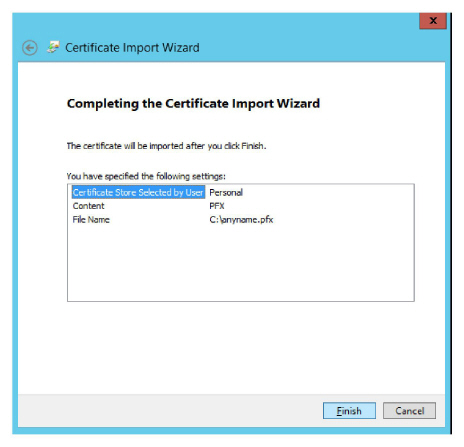
10.The certificate file will be copied onto the operating system of the current computer.
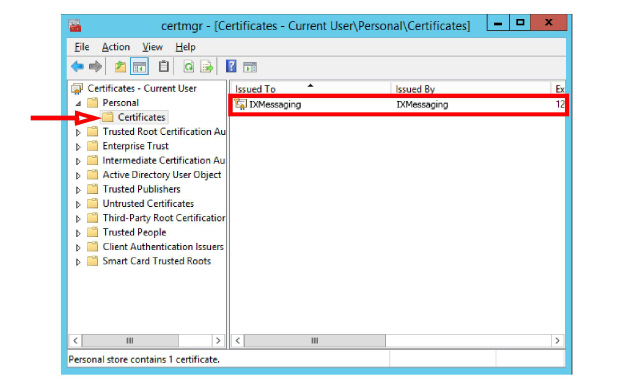
The certificate file has been successfully restored.
Reboot the server to have the changes take effect.
To enable an HTTPS connection, another certificate has to be installed in IIS. This certificate must be acquired from a certifying authority.
The HTTPS protocol must be enabled, and HTTP disabled.
1.On the computer that functions as the web server, open the IIS Manager console.
Select the local computer. Open Server Certificates in the right-hand pane.
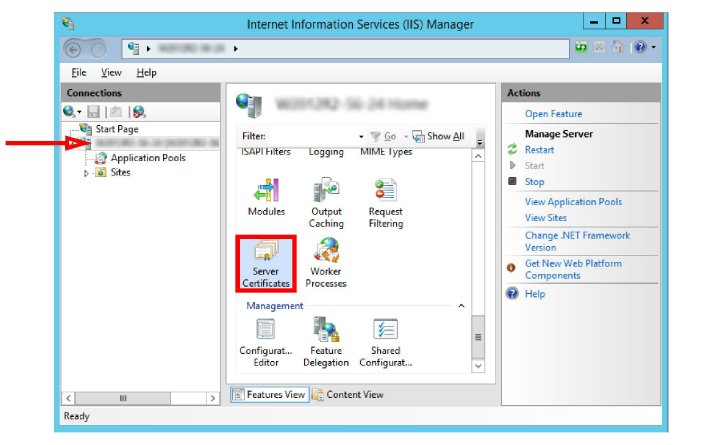
2.Right-click in the right-hand pane and choose Import from the pop-up menu.
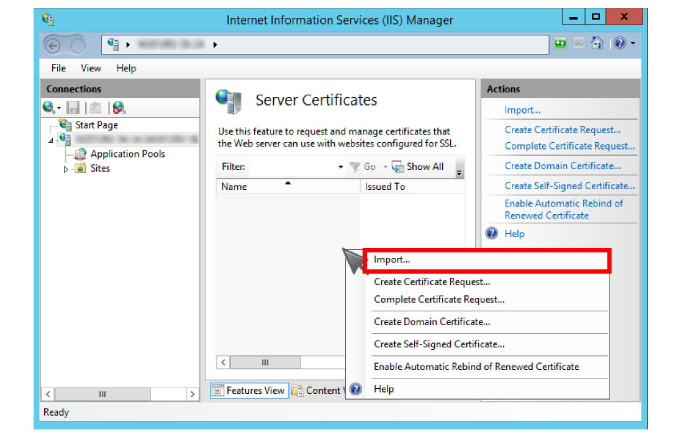
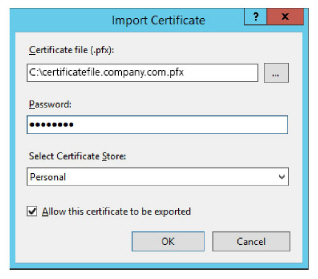
3.Enter the path to the certificate file and the password. Select Personal as the Certificate Store. Click OK.
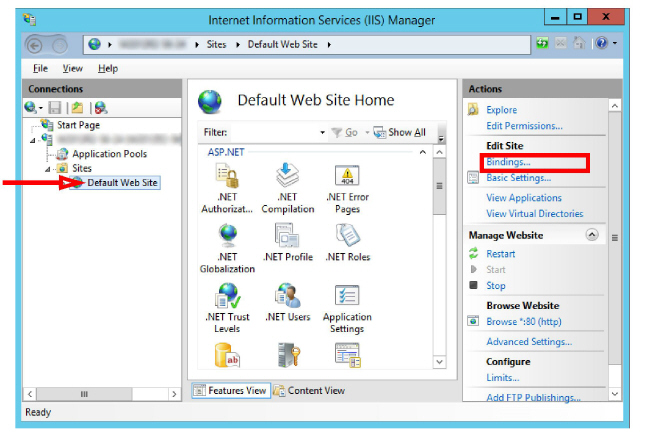
4.Go to Sites > Default Web Site.
Click Bindings....
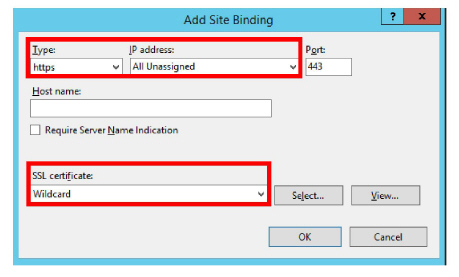
5.Add the HTTPS binding type.
Set the IP Address to All Unassigned. Leave Port at its default.
Change SSL Certificate to the certificate name installed above.
Click OK.
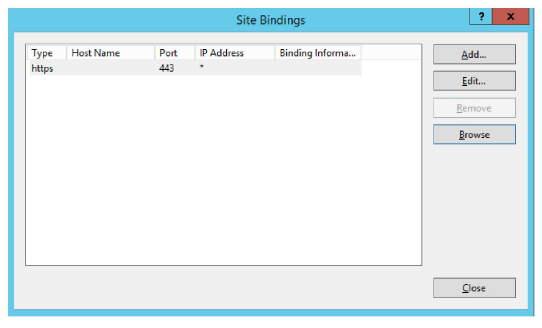
6.Remove HTTP from the list of bindings.
Click Close.
Disabling User Account Control Notification
1.Go to Settings > Control Panel. Select User Accounts.
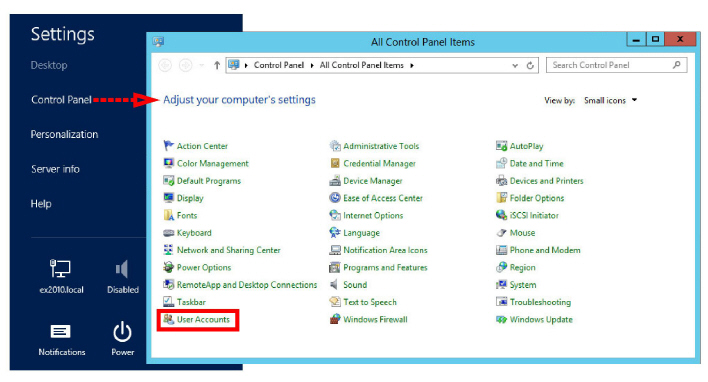
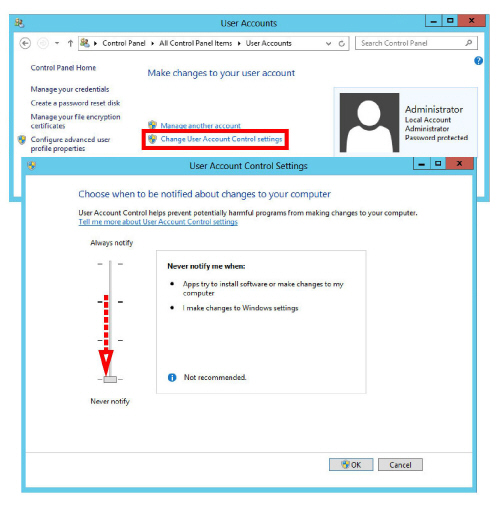
2.Select Change Account Settings.
On the User Account Control Settings screen, click and drag the slider down to Never Notify.
Click OK and Close.
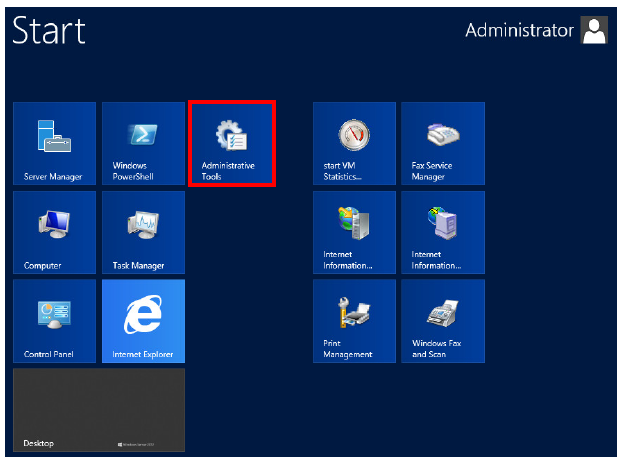
3.On the keyboard, click the Start button, and select Administrative Tools.
4.Double-click Local Security Policy.
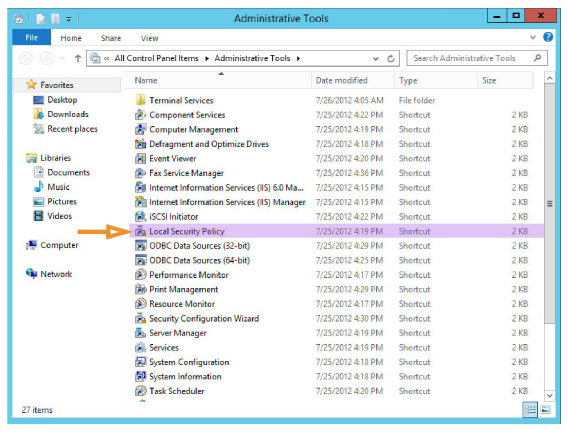
5.Under Security Settings > Local Policies > Security Options, double-click
User Account Control: Run all administrators in Admin Approval Mode.
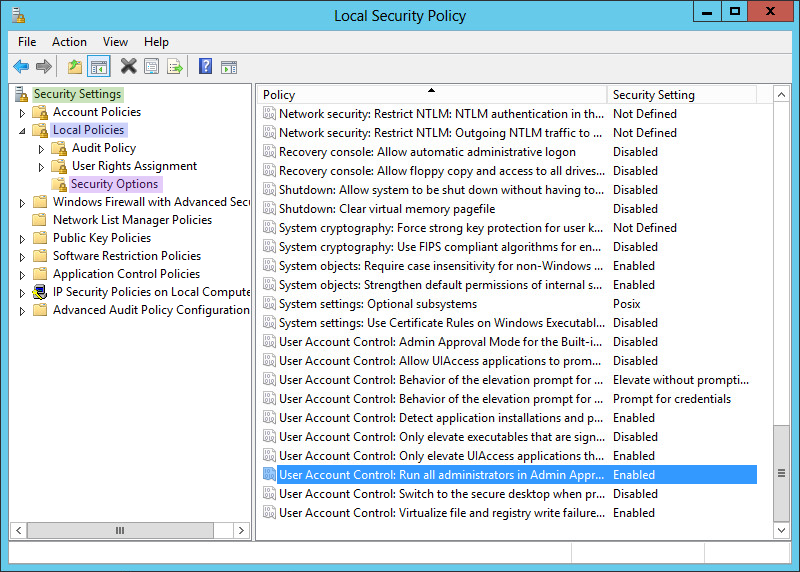
6.Select Disabled. Click OK.
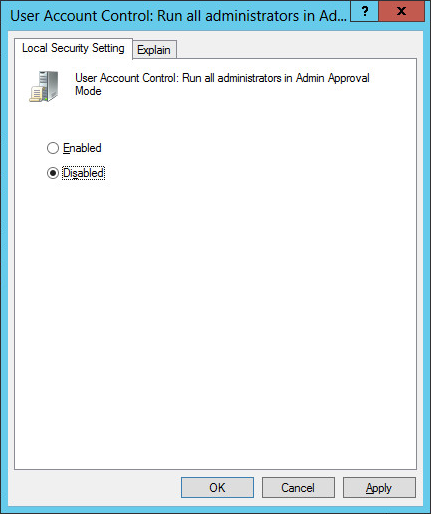
7.Reboot the server.
|
Note: UAC Notifications can be restored after Messaging has been installed. |
Install Microsoft .Net Framework 4.7.2
Avaya IX Messaging requires Microsoft .Net Framework version 4.7.2 to be installed to support various features within the program. If it has not already been installed, the administrator must download it and install it manually.
|
Note: .Net Framework 4.7.2 is not installed by default. It may be part of Windows updates, optional updates, or not provided at all. Follow these instruction is it is not installed on your system, or if you do not know if it has been installed. |
1.Open a web browser and go to the Microsoft web site. Search for .Net Framework 4.7.2 and install the application on the server. For example:
https://support.microsoft.com/en-us/help/4054531/microsoft-net-framework-4-7-2-web-installer-for-windows .
2.Download the file to your server drive. When ready, run the program to install this feature.
When finished, restart the server.
Installing Messaging for JITC on a Single Server
This section covers installing Messaging in Single Server configuration. If you are planning a High Availability installation, jump to here.
Continue with the Avaya IX Messaging installation. The presence of a JITC license will be noted during installation and the appropriate files will be loaded. Encryption will be automatically enabled at that time.
|
Note: Make sure that all of the necessary Services for your operating system have been installed before proceeding with the installation. Refer to the appropriate section of the Server Installation Guide for details. Also make sure that Windows Firewall is disabled, and that Windows Automatic Update is turned off. |
1.Download the installation file (see chapter 4). Run the file (double-click) to extract the contents. Specify the location on your hard drive where you want to save the files.
2.In the extraction folder, run Setup.exe as administrator to install Avaya IX Messaging onto your voice server.
3.Once the Windows components have been verified, click Next to begin the installation.
|
Note: The installer will automatically install the necessary packages at the beginning of the installation if they do not already exist on the system. These packages may include Sentinel Protection, Microsoft Visual C++ Redistributable and Microsoft .Net Framework 4.5. This process may take a while depending on the required components. |
|
Note: Clicking on the Documentation button will provide you with the default set of PDF documents which comprehensively cover most aspects of Messaging. They can also be downloaded from resources.zang.io in both PDF and HTML format. |
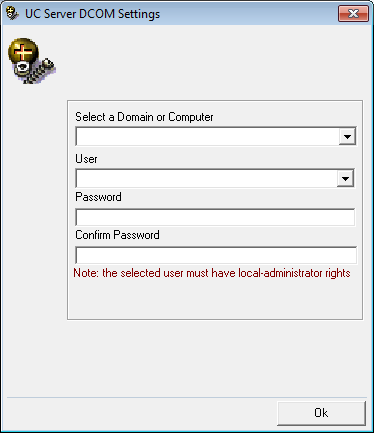
4.Enter the DCOM user info (domain user account which has local administrator rights). This is required by services which use local administrator rights.
Click OK after entering the necessary credentials.
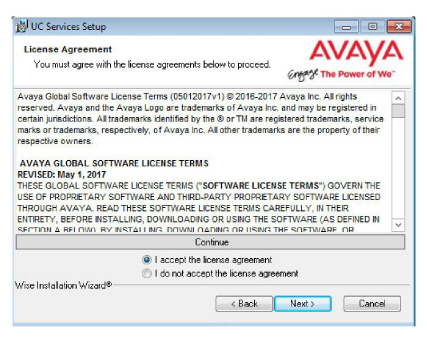
5.Review all the license agreements and select
I accept the license agreement.
Click Next to continue.
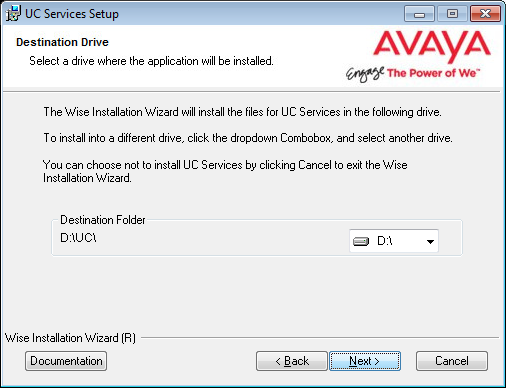
6.You will be asked to select the destination of the installation. You may change the hard drive destination through the drop down menu. By default, the installation will create a UC folder on the C drive.
Click Next to continue.
|
Note: It is highly recommended that you install the program to a drive other than C to prevent any conflicts or performance issues. |
7.Enable Single UC Server.
Click Next.
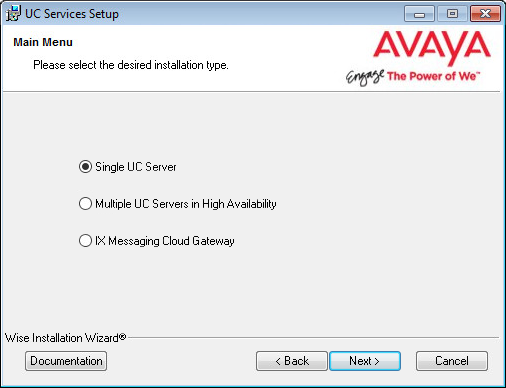
Single UC Server: When operating Messaging on a single server computer.
Multiple UC Servers in High Availability: When running Messaging in High Availability mode for redundancy.
IX Messaging Cloud Gateway: Gateway allows end-to-end synchronization between the Avaya Aura Messaging server and Google's Gmail using Avaya IX Messaging message sync and the CSE. Refer to chapter 15, Install and Configure Cloud Gateway for complete details.
8.Select the license type you will using for this installation.
Most sites will use the WebLM License option.
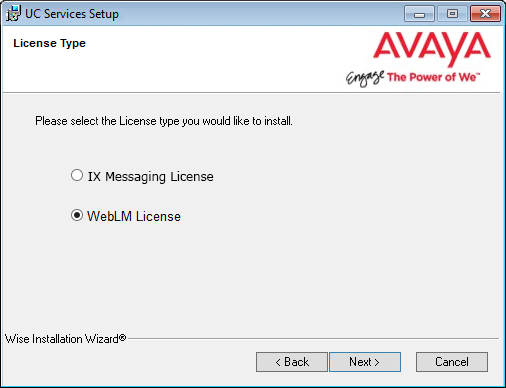
|
Note: If you select Messaging, go to chapter 12, Installing the Messaging License. When finished, return here and continue the installation from step 11. Skip step 9 through 10. |
|
Warning: It is essential that the system/PC clock be properly set before activating the license. Any subsequent changes to the clock can adversely affect or terminate the license. |
9.The License Upgrade Utility program opens and prompts you to enter the IP Address for the computer that houses the WebLM license engine.
Enter the address in the space provided, then click OK.
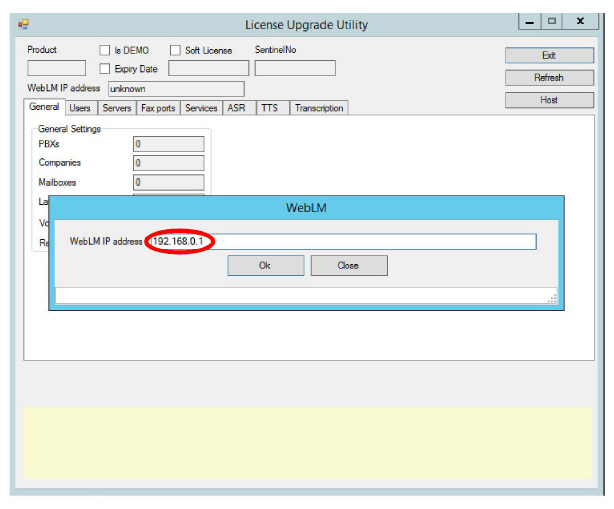
|
Important: This step requires that the Web License Manager has been installed and configured on the license server computer. See Installing the WebLM License and Server on page 437. |
10.The utility will retrieve your license details from the server and display them here. Review the license details and click Exit when ready.
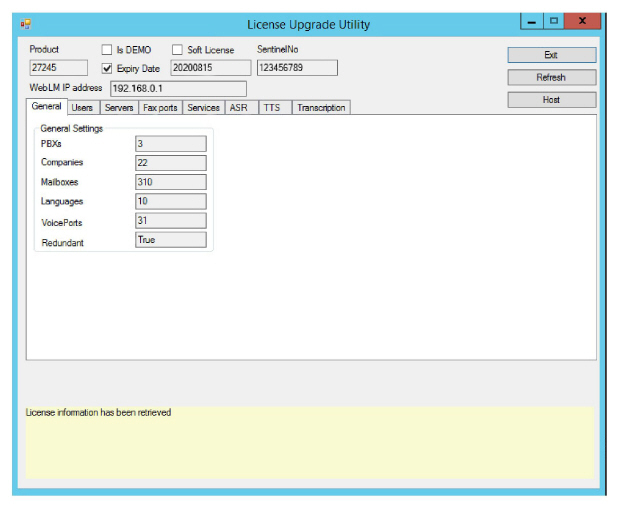
|
Note: The number of voice ports is calculated based upon your license. |
11.Select the Components required at your site. Disable any components that are not needed.
Click Next.
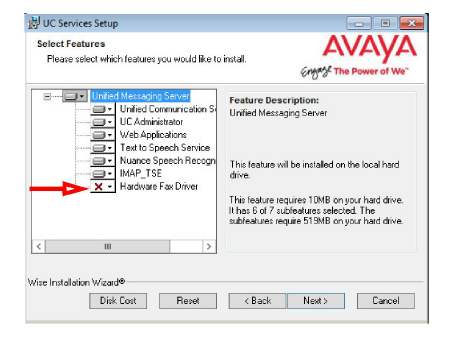
12.This screen shows all of the Windows roles and features that Messaging requires to operate properly.
|
Note: This screen will only appear if one or more required components are not installed on the computer. |
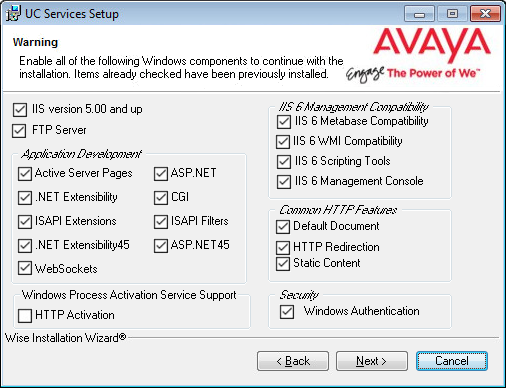
For all items that are not checked, return to Windows and add any missing pieces to the operating system.
Click Next when finished or to refresh the display.
|
Note: The installation will not continue until all of the required components have been added to Windows. |
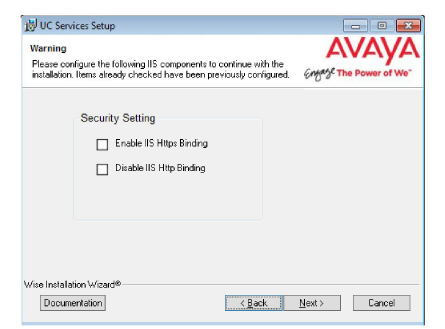
13.This screen shows IIS settings that Messaging requires to operate properly.
|
Note: This screen will only appear if one or more of the required settings has not been made on the computer. |
For all items that are not checked, return to the IIS Manager in Windows and set these options as required.
Click Next when finished or to refresh the display.
|
Note: The installation will not continue until all of the required IIS settings have been made. |
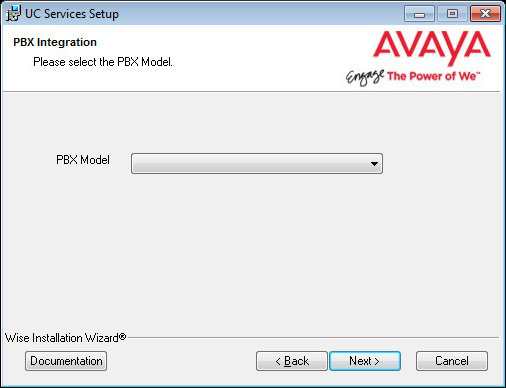
14.Select your PBX Brand then click Next.

15.Select your PBX model from the dropdown menu.
Click Next.
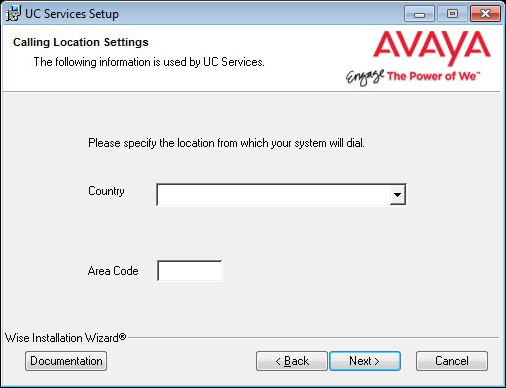
16.Enter the primary location from which most telephone calls will be placed. This will normally be where the corporate office is situated. Additional dialing locations and rules may be defined after the installation is complete.
Select the country from the dropdown menu, and enter the area code in the space provided.
Click Next to continue.
|
Note: If the Phone and Modem Settings under Windows Control Panel have already been configured, this step will not appear. The values entered there will be used automatically. |
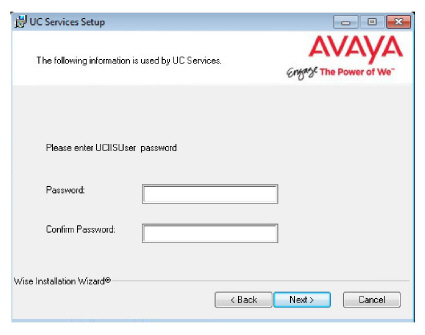
17.Create and verify a UC IIS User Password. This is used when logging into any associated web applications, such as Web Access.
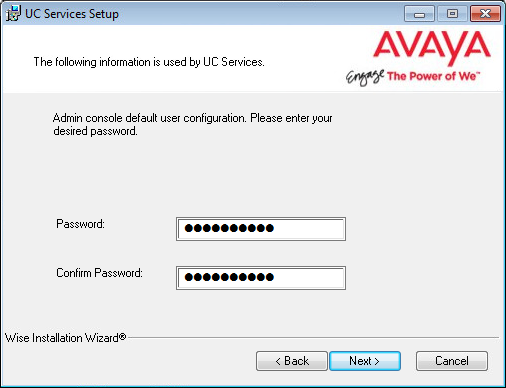
18.Enter a password to provide administrator only access to the system. This account password is used to configure the many elements of the system.
|
Hint: The password cannot be left blank. It must contain both letters, numbers and characters, and must be at least 15 characters long. See here for a complete list of password requirements. |
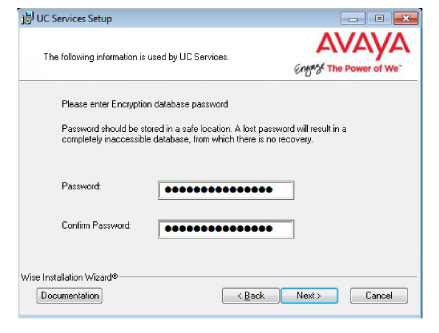
19.Enter the database encryption password. The database files will be encrypted with this password using the FIPS 140-2 certified security algorithms.
This password must meet the requirements outlined here.
|
Important: Record this password and keep it in a safe location. |
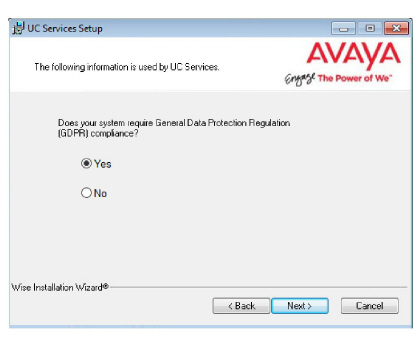
20.Choose either Yes or No to determine whether the system will apply General Data Protection Regulation (GDPR) compliance procedures to your data.
With this option enabled, users and callers are notified that personal information will be collected. This information can also be completely removed from the system upon request.
21.The preliminary information required for installation is now complete.
Click Next.

22.The selected components will now be installed. This process may take a while.
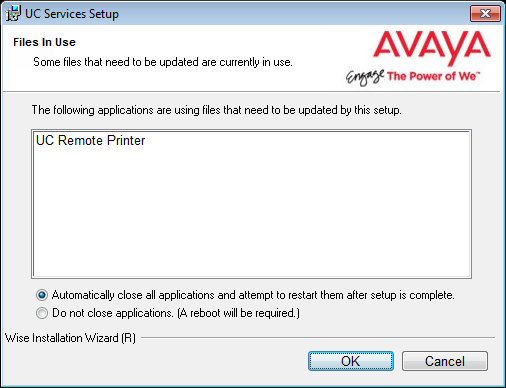
23.If you are warned about components being in use, either use the Automatic Close option or manually close the process which is interfering with the installation.
Click OK when ready.
24.After all the components are copied, you may be asked to provide the settings for the PBX that you have chosen. Since this process varies greatly from system to system, please ensure that you configure your site’s PBX exactly as required.
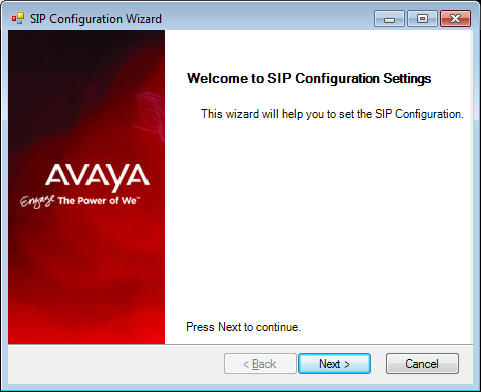
25.In this section of the installation wizard you will be asked to provide additional settings for SIP integration.
Click Next to continue.
26.Fill out all required information. The PBX and the Number of Channels fields are automatically populated. Enter the IP Address of the PBX.
Trunk is selected by default, and is the best option for most installations.
Select Extension if it is available through the PBX, and if Pre-Paging is required. If Extension is enabled, enter the Start Extension Number established during PBX setup.
Click Next when ready.

27.Confirm the information then click Finish.
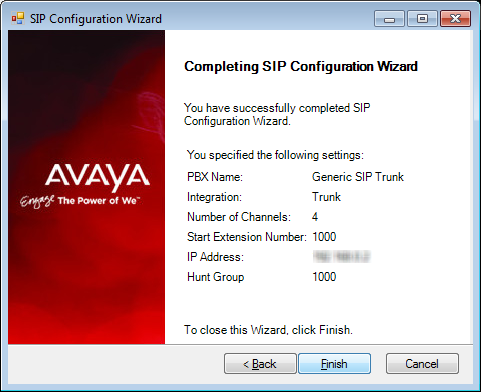
|
Note: Depending on the type of SIP integration you’ll be using, you may have to fine tune the settings from the SIP Configuration Tool in order for the system to function properly. The SIP Configuration Tool can be found in the Messaging programs folder after installation. |
28.On the SSO Configuration screen, enable Legacy SSO. From the dropdown menu, enable the Providers that you want your clients to be able to use to access Web Admin, Messaging Admin, Web Access, and Web Reports. Items that are disabled will not appear during client login.
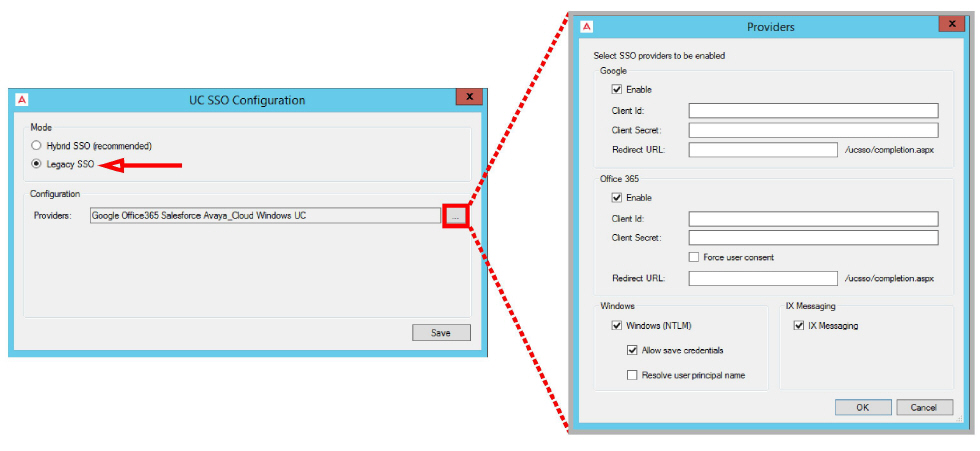
When clients / admins want access to these programs, they login using their credentials for one of the listed programs. They must have an account with that application before they can login.
Enable all that apply, then click OK.
Click Save when finished.
|
Important: The Hybrid SSO login procedure requires an active Internet connection. Only Legacy SSO can be used if Internet access is disabled / locked-down. |
|
Note: For complete details on using legacy and hybrid SSO, refer to chapter 25 of this document. |
29.Click Finish to restart the server.
If you wish to restart your computer at a later time, disable the Restart check box then click Finish.
30.Verify that the Encryption File System (EFS) certificate has been saved to another secure location (see Backup and Restore the Certificate File on page 287). If the certificate becomes corrupted, UC Communication will no longer function and are unrecoverable without this backup file.
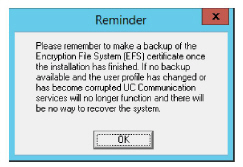
Click OK to restart the computer.
Installing Messaging for JITC with High Availability
This section covers installing Messaging for JITC in a High Availability (HA) configuration. If you are planning a Single Server installation, jump to here.
An HA installation involves up to 21 servers: 1 Primary voice server, 1 Consolidated server, and up to 19 Secondary servers. The program must be installed and configured on all 3 types of server. If any of the servers fail, the remaining servers take over with no interruption in service. The multiple server configuration also spreads large traffic loads across many machines to improve performance.
Continue with the Avaya IX Messaging installation.
|
Important: The presence of a JITC license will be noted by the Wizard during installation and the appropriate files will be loaded. Encryption will be automatically enabled at that time. |
The installation process for each type of server is slightly different and each will be covered separately here:
|
Warning: It is important to login to the servers (Primary, Consolidated and all Secondaries) using a domain account that has full administrative rights on the local machine. |
|
Note: Make sure that all of the necessary Services for your operating system have been installed before proceeding with the installation. Refer to the appropriate section of the Server Installation Guide for further details. Also make sure that Windows Firewall is disabled, and that Windows Automatic Update is turned off. |
1.Download the installation file (see chapter 4). Run the file (double-click) to extract the contents. Specify the location on your hard drive where you want to save the files.
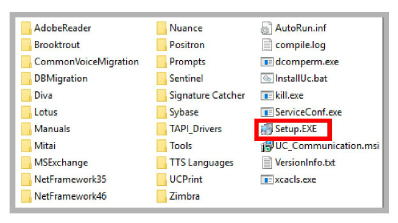
2.In the extraction folder, run Setup.exe as administrator to install Avaya IX Messaging onto the Primary server.
3.Once the Windows components have been verified, click Next to begin the installation.
|
Note: The installer will automatically add the necessary components if they do not already exist on the system. These packages may include Sentinel Protection, Microsoft Visual C++ Redistributable and Microsoft .Net Framework 4.5. This process may take a while depending on the required components. |
|
Note: Clicking on the Documentation button will provide you with the default set of PDF documents which comprehensively cover most aspects of Messaging. They can also be downloaded from resources.zang.io in both PDF and HTML format. |
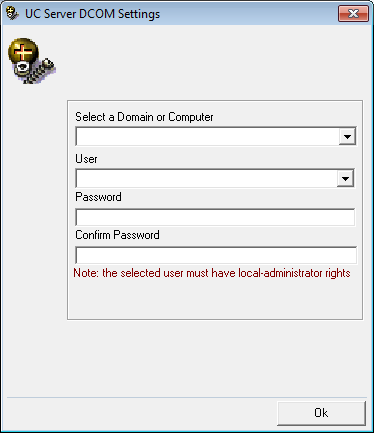
4.Enter the DCOM user info (domain user account which has local administrator rights). This is required by services which use local administrator rights.
Click OK after entering the necessary credentials.
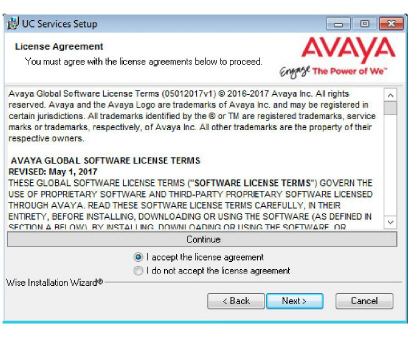
5.Review the license agreement and select
I accept the license agreement.
Click Next when ready.
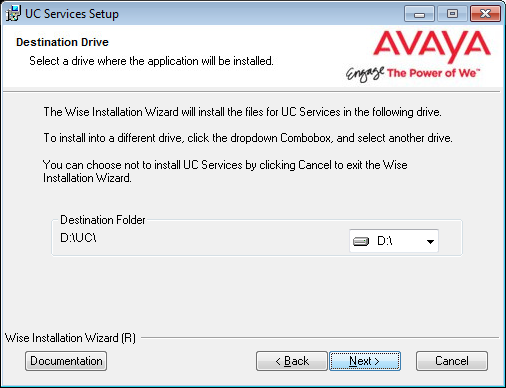
6.You will be asked to select the destination of the installation. You may change the hard drive destination through the drop down menu. By default, the installation will create a UC folder on the C drive.
Click Next to continue.
|
Note: It is highly recommended that you install the program to a drive other than C to prevent any conflicts or performance issues. |
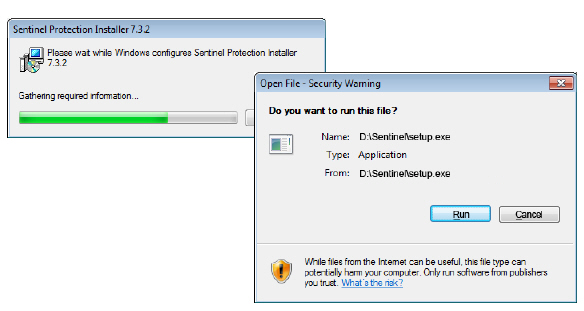
7.Enable Multiple UC Servers in High Availability.
Click Next.
Single UC Server: When operating Messaging on a single server computer.
Multiple UC Servers in High Availability: When running Messaging in High Availability mode for redundancy.
IX Messaging Cloud Gateway: Gateway allows end-to-end synchronization between the Avaya Aura Messaging server and Google's Gmail using Avaya IX Messaging message sync and the CSE. Refer to chapter 15, Install and Configure Cloud Gateway for complete details.

8.Select Primary Voice Server.
Click Next.
9.When prompted, click Run to confirm the installation. The necessary files will be installed.
|
Note: This screen may not appear, depending upon your system settings. |
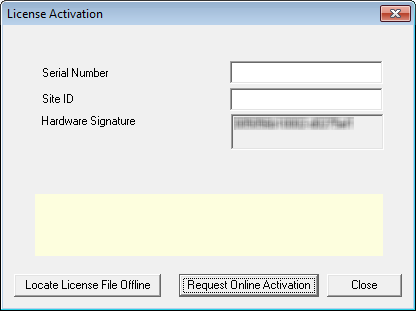
10.Once the process is complete the licensing screen will appear. It is recommended that you use Online Activation whenever possible. To do so, simply enter the Serial Number and Site ID .
Click Request Online Activation when finished.
|
Warning: It is essential that the system/PC clock be properly set before activating the license. Any subsequent changes to the clock can adversely affect or terminate the license. |
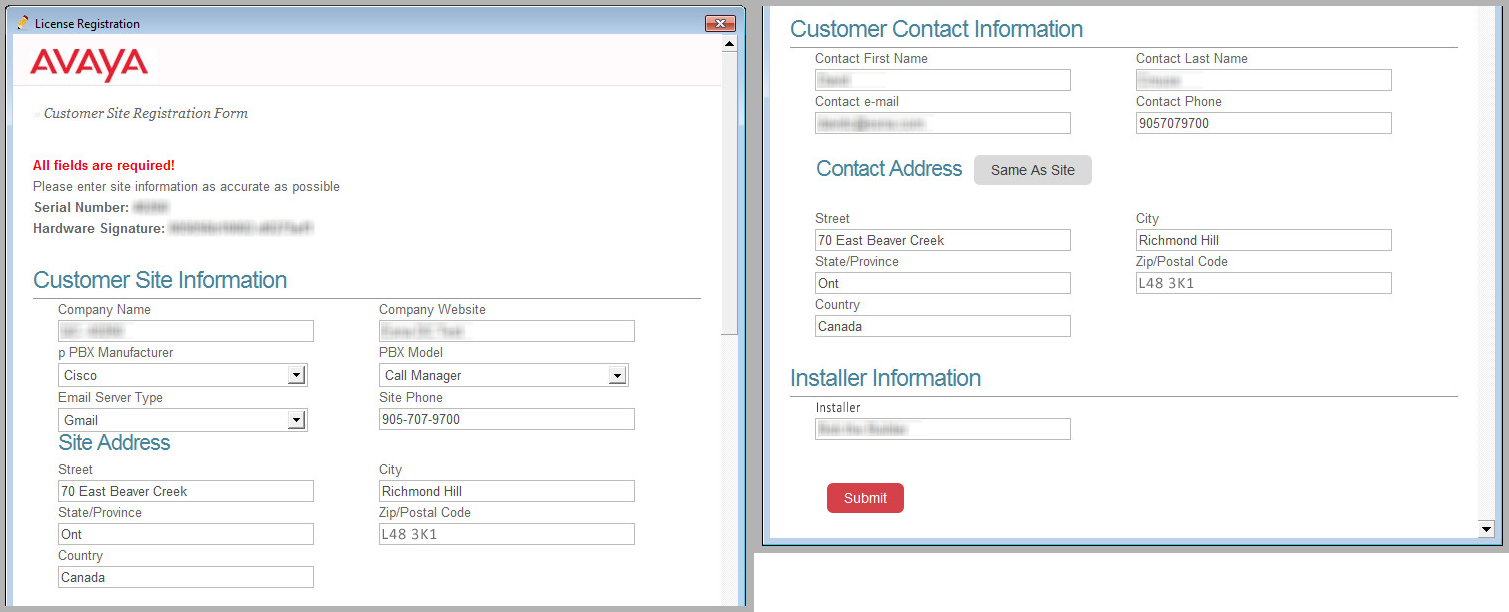
11.Most of the fields in the Customer Site Registration window should already be filled in based upon the license and site numbers entered. Complete the form where necessary (all fields are required).
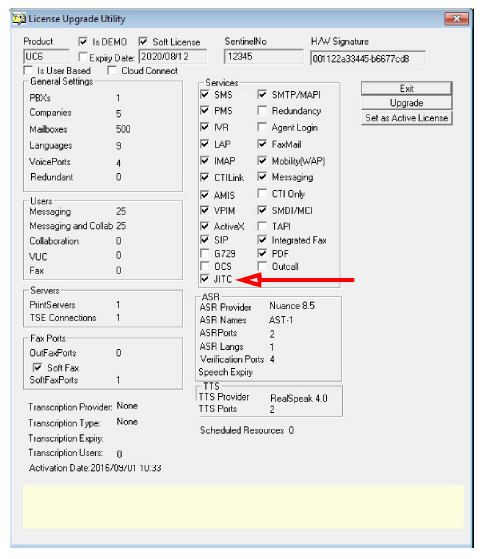
12.Confirm the contents of your license then click on the Set as Active License button.
|
Caution: Verify that the JITC checkbox has been enabled. If it is blank, pause the installation immediately and contact your dealer. The license must be upgraded before you continue. |
|
Note: Whenever your license is updated after the initial installation (e.g. through the addition of new features, extensions, etc.) please restart the server after activating the license so that the new parameters can become active. |
13.If the process was successful the following confirmation screen will appear.
Click OK.

14.Click Exit to close the license window and continue with the installation.
15.This reminder may appear.
Click OK.

16.Select the Components required at your site.
Click Next.
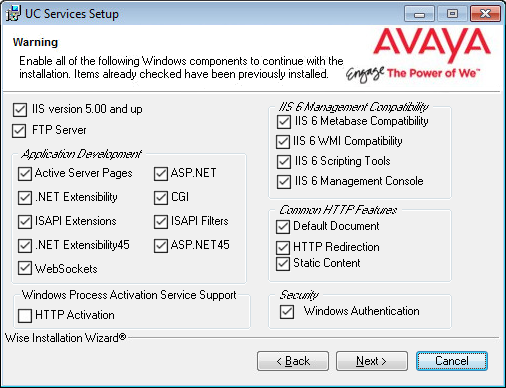
17.This screen shows all of the Windows roles and features that Messaging requires to operate properly.
|
Note: This screen will only appear if one or more required components are not installed on the computer. |
For all items that are not checked, return to Windows and add any missing pieces to the operating system.
Click Next when finished.
|
Note: The installation will not continue until all of the required components have been added to Windows. |
18.This screen shows IIS settings that Messaging requires to operate properly.
|
Note: This screen will only appear if one or more of the required settings has not been made on the computer. |
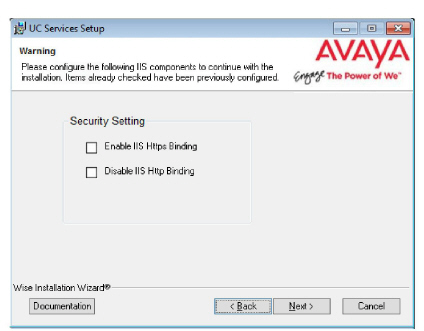
For all items not checked, refer to IIS Certificate Bindings for configuration details.
Click Next when finished.
|
Note: The installation will not continue until all of the required IIS settings have been made. |
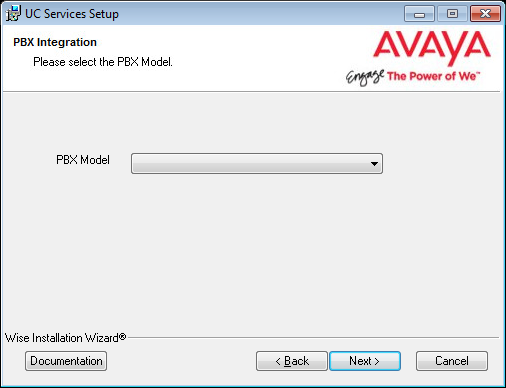
19.Select your PBX Brand then click Next.

20.Select your PBX model from the dropdown menu.
Click Next.
21.Enter the IP Address for the Consolidated Server.
Click Next.
22.Enter the number of ports your system will use.
Click Next.
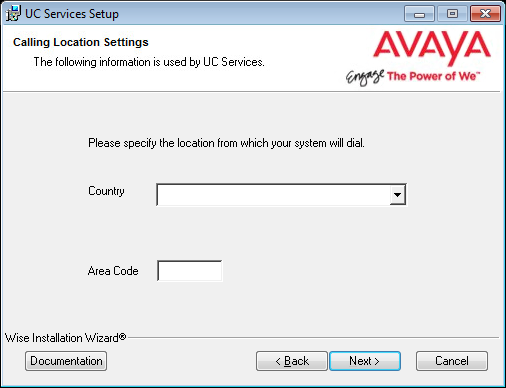
23.Enter the primary location from which most telephone calls will be placed. This will normally be where the corporate office is situated. Additional dialing locations and rules may be defined after the installation is complete.
Select the country from the dropdown menu, and enter the area code in the space provided.
Click Next to continue.
|
Note: If the Phone and Modem Settings under Windows Control Panel have already been configured, this step will not appear. The values entered there will be used automatically. |
24.Create and verify a UC IIS User Password. This is used when logging into any associated web applications, such as Web Access.
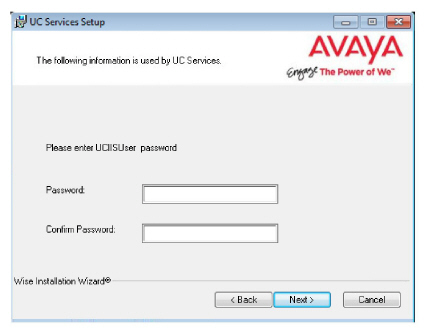
25.Enter the database encryption password. The database files will be encrypted with this password using the FIPS 140-2 certified security algorithms.

|
Important : Record this password and keep it in a safe location. |
26.Enter the values in the spaces provided. These are provided with the certificate (either self-signed or a CA signed).
These values are used when configuring the certificates on here.
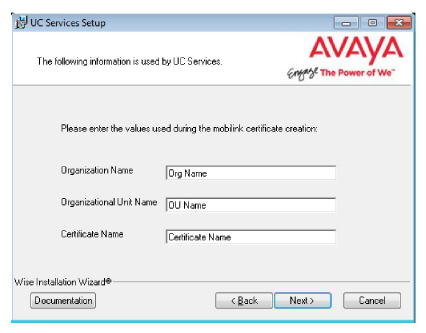
27.The preliminary information required for installation is now complete.
Click Next.
28.The selected components will now be installed. This process may take a while.
29.If you are warned about components being in use, either use the automatic option or manually close the process which is interfering with the installation.
Click OK when ready.
30.After all the components are copied, you may be asked to provide the settings for the PBX that you have chosen. Since this process varies greatly from system to system, please ensure that you configure your site’s PBX exactly as required.
31.In this section of the installation wizard you will be asked to provide additional settings for SIP integration.
Click Next to continue.

32.Fill out all required information. The PBX and the Number of Channels fields are automatically populated. Enter the IP Address of the PBX.
Trunk is selected by default, and is the best option for most installations.
Select Extension if it is available through the PBX, and if Pre-Paging is required. If Extension is enabled, enter the Start Extension Number established during PBX setup.
Click Next when ready.
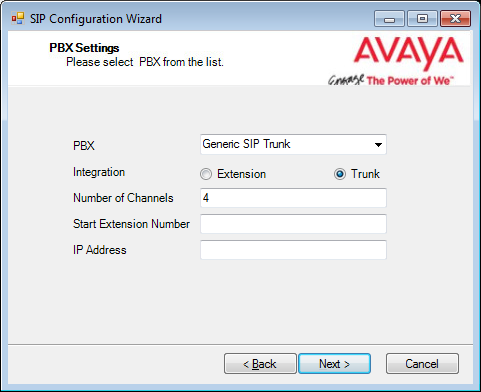
33.Confirm the information then click Finish.
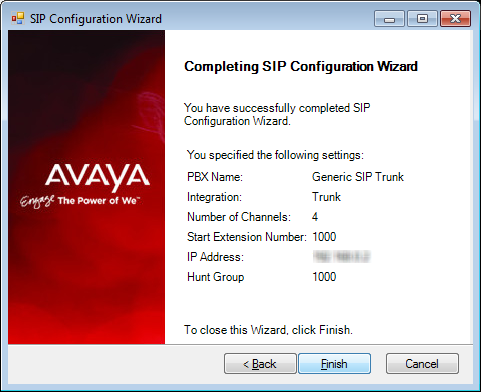
|
Note: Depending on the type of SIP integration you’ll be using, you may have to fine tune the settings from the SIP Configuration Tool in order for the system to function properly. The SIP Configuration Tool can be found in the Messaging programs folder after installation. |
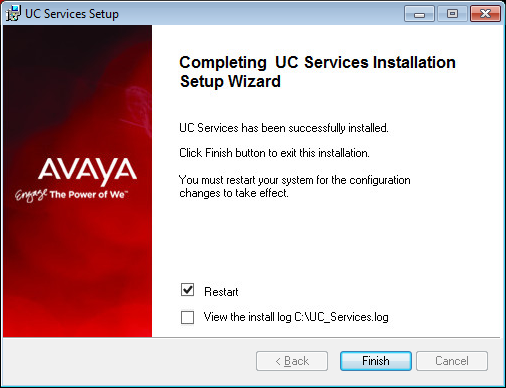
34.Click Finish to restart the server.
If you wish to restart your computer at a later time, disable the Restart check box then click Finish.
35.This alert is to remind you to properly share the UC installation folder (see here for details).

|
Important: The installation folder MUST be shared before proceeding with the Consolidated and Secondary server installations. |
36.Verify that the Encryption File System (EFS) certificate has been saved to another secure location (see Backup and Restore the Certificate File on page 287). If the certificate becomes corrupted, UC Communication will no longer function and are unrecoverable without this backup file.
Click OK to restart the computer.
|
Note: Make sure that all of the necessary Services for your operating system have been installed before proceeding with the installation. Refer to the appropriate section of the Server Installation Guide for further details. Also make sure that Windows Firewall is disabled, and that Windows Automatic Update is turned off. |
1.Download the installation file (see chapter 4). Run the file (double-click) to extract the contents. Specify the location on your hard drive where you want to save the files.
2.In the extraction folder, run Setup.exe as administrator to install Avaya IX Messaging onto your Consolidated server.
3.Once the Windows components have been verified, click Next to begin the installation procedure.
|
Note: The installer will automatically install the necessary packages at the beginning of the installation if they do not already exist on the system. These packages may include Sentinel Protection, Microsoft Visual C++ Redistributable and Microsoft .Net Framework 4.5. This process may take a while depending on the required components. |
|
Note: Clicking on the Documentation button will provide you with the default set of PDF documents which comprehensively cover most aspects of Messaging. They can also be downloaded from resources.zang.io in both PDF and HTML format. |
4.Enter the DCOM user info (domain user account which has local administrator rights). This is required by services which use local administrator rights.
Click OK after entering the necessary credentials.

5.Review all the license agreements and select
I accept the license agreement.
Click Next to continue.
6.You will be asked to select the destination of the installation. You may change the hard drive destination through the drop down menu. By default, the installation will create a UC folder on the C drive.
Click Next to continue.
|
Note: It is highly recommended that you install the program to a drive other than C to prevent any conflicts or performance issues. |
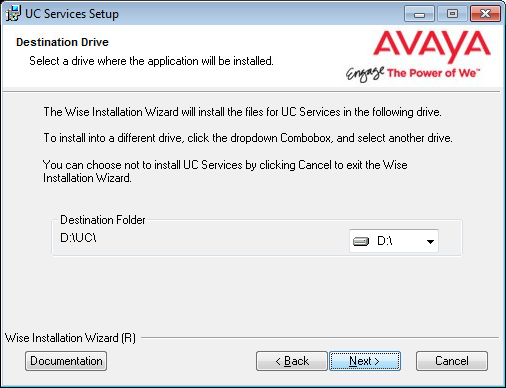
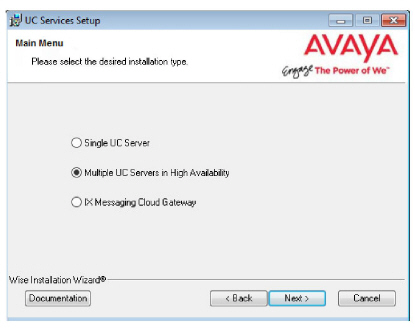
7.Enable Multiple UC Servers in High Availability.
Click Next.
Single UC Server: When operating Messaging on a single server computer.
Multiple UC Servers in High Availability: When running Messaging in High Availability mode for redundancy.
IX Messaging Cloud Gateway: Gateway allows end-to-end synchronization between the Avaya Aura Messaging server and Google's Gmail using Avaya IX Messaging message sync and the CSE. Refer to chapter 15, Install and Configure Cloud Gateway for complete details.
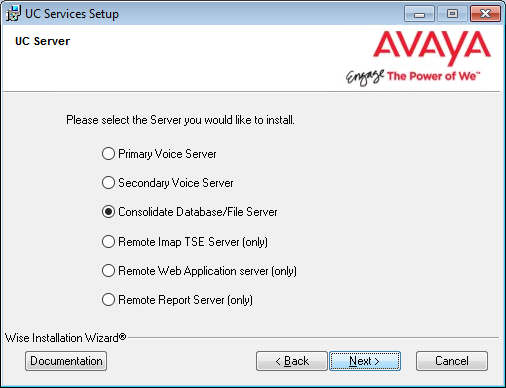
8.Select Consolidated Database/File Server.
Click Next.
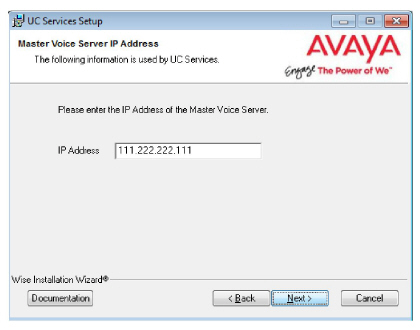
9.Enter the IP address for the Primary voice server.
Click Next.
10.On the C drive, open the Logs folder.
Open the file named icense using any text editor (e.g. Notepad).
Verify Highsecurity=1. If it does not, verify that the same file (IXM Installation drive:\UC) on the Primary voice server does have this setting. If the setting is valid on the Primary, there is a connection or a sharing problem between the two machines. If the Primary is not correctly set, contact your reseller for an updated license.
Once any connection or sharing problems have been fixed, return to step 9 and check again for this file.
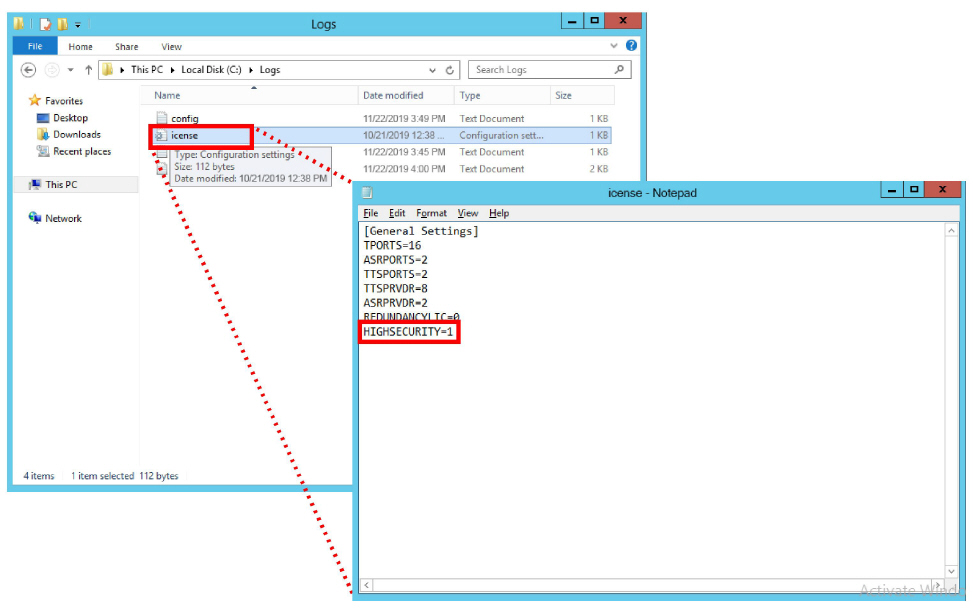
|
Caution: Do not continue the installation until this file has the Highsecurity setting equal to 1. |
11.Select the Components required at your site.
Click Next.
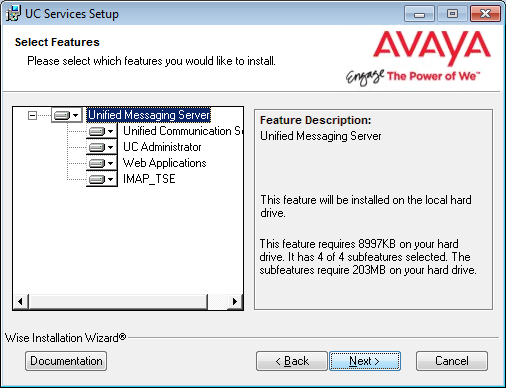
12.This screen shows all of the Windows roles and features that the Consolidated server requires to operate properly.
|
Note: This screen will only appear if one or more required components are not installed on the server. |
For all items that are not checked, return to Windows and install any missing pieces into the operating system.
Click Next when finished.
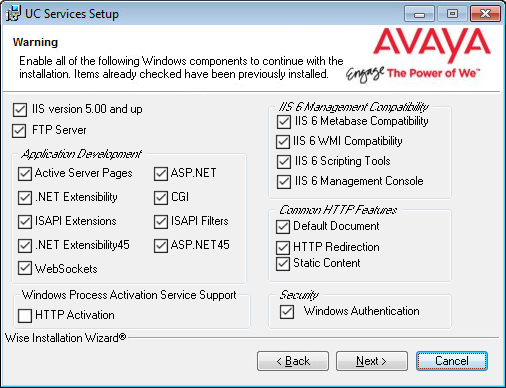
|
Note: The installation will not continue until all of the required components have been added to the server. The screen does not refresh until you click Next. |
13.Select your PBX Brand then click Next.

14.Select your PBX model from the dropdown menu.
Click Next.
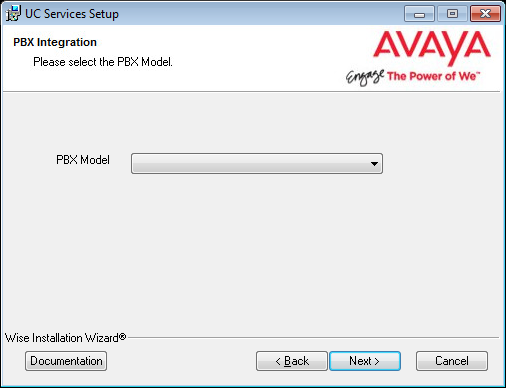
15.Unless the Primary Server has been upgraded, enable No.
Click Next.
16.Enter a password to provide administrator only access to the system. This account password is used to configure the many elements of the system.
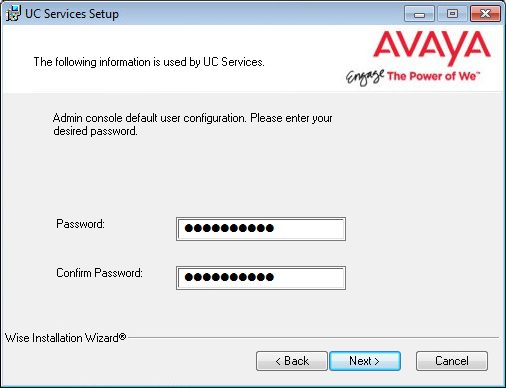
|
Hint: Passwords cannot be left blank. In a JITC installation, all passwords must contain letters, numbers and characters, and must be at least 15 characters long. See here for a complete list of password requirements. |
17.Create and verify a UC IIS User Password. This is used when logging into any associated web applications, such as Web Access.
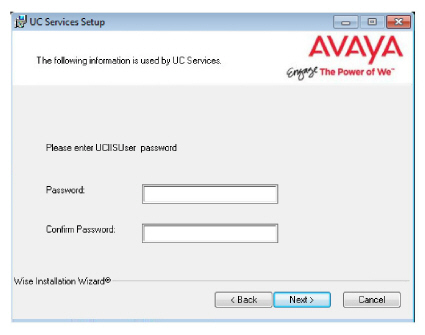
18.Enter the database encryption password. The database files will be encrypted with this password using the FIPS 140-2 certified security algorithms.
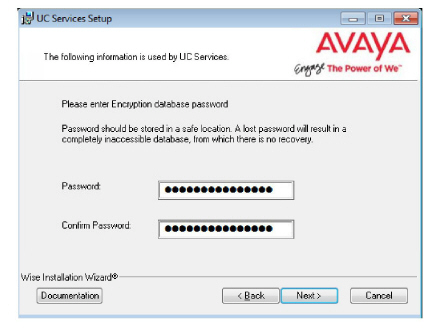
|
Important: Record this password and keep it in a safe location. |
19.Enter an encryption password to protect Mobilink communications.
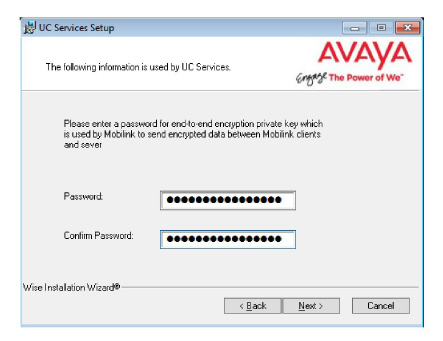
20.Enter a password for the Mobilink identity file.
Click Next.
21.The preliminary information required for installation is now complete.
Click Next.
22.The selected components will now be installed. This process may take a while.
23.If you are warned about components being in use, either use the Automatically Close option or manually close the process which is interfering with the installation.
Click OK when ready.
24.After all the components are copied, you may be asked to provide the settings for the PBX that you have chosen. Since this process varies greatly from system to system, please ensure that you configure your site’s PBX exactly as required.
25.On the SSO Configuration screen, enable Legacy SSO. From the dropdown menu, enable the Providers that you want your clients to be able to use to access Web Admin, Messaging Admin, Web Access, and Web Reports. Items that are disabled will not appear during client login.
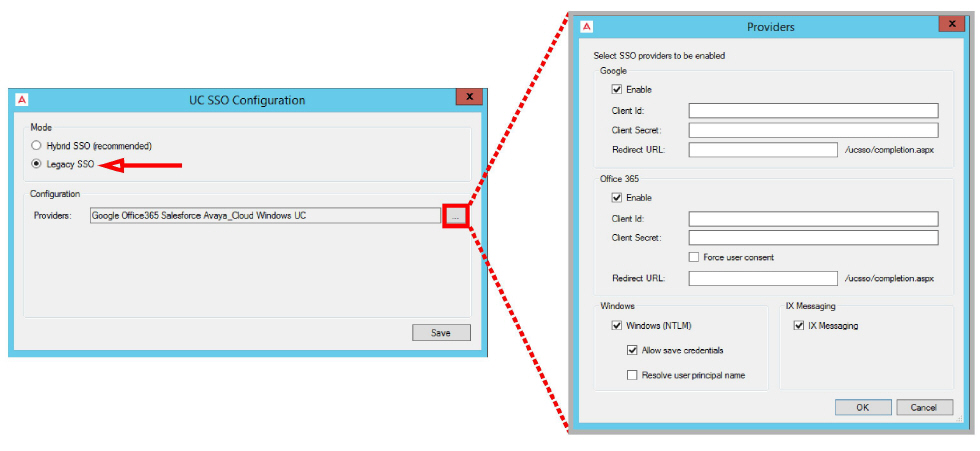
When clients / admins want access to these programs, they login using their credentials for one of the listed programs. They must have an account with that application before they can login.
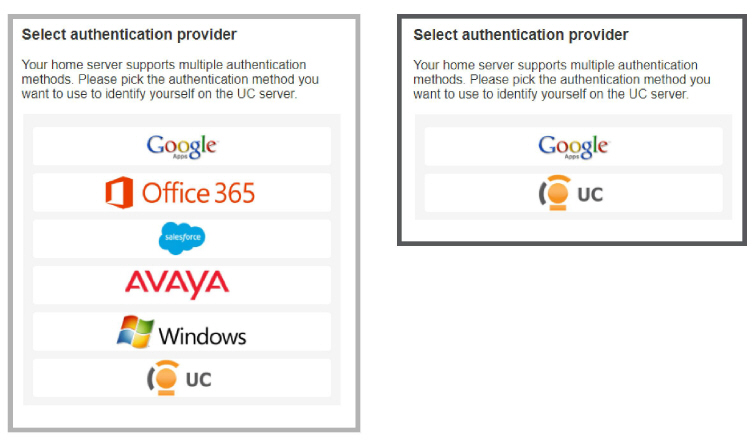
Enable all that apply, then click OK.
Click Save when finished.
|
Important: The Hybrid SSO login procedure requires an active Internet connection. Only Legacy SSO can be used if Internet access is disabled / locked-down. |
|
Note: For complete details on using legacy and hybrid SSO, refer to chapter 25 of this document. |
26.Click Finish to restart the server.
If you wish to restart your computer at a later time, disable the Restart check box then click Finish.
27.This alert is to remind you to properly share the UC installation folder (see here for details).

|
Important: The installation folder MUST be shared before proceeding with the Consolidated and Secondary server installations. |
28.Verify that the Encryption File System (EFS) certificate has been saved to another secure location (see Backup and Restore the Certificate File on page 287). If the certificate becomes corrupted, UC Communication will no longer function and are unrecoverable without this backup file.
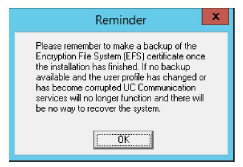
Click OK to restart the computer.
Up to 19 Secondary servers can be added to a High Availability environment. Each must be given its own, unique identification number (e.g. 2-20) which is assigned during installation.
|
Note: Make sure that all of the necessary Services for your operating system have been installed before proceeding with the installation. Refer to the appropriate section of the Server Installation Guide for further details. Also make sure that Windows Firewall is disabled, and that Windows Automatic Update is turned off. |
1.Download the installation file (see chapter 4). Run the file (double-click) to extract the contents. Specify the location on your hard drive where you want to save the files.
2.In the extraction folder, run Setup.exe as administrator to install Avaya IX Messaging onto all of your Secondary servers.
3.Once the Windows components have been verified, click Next to begin the installation procedure.
|
Note: The installer will automatically install the necessary packages at the beginning of the installation if they do not already exist on the system. These packages may include Sentinel Protection, Microsoft Visual C++ Redistributable and Microsoft .Net Framework 4.5. This process may take a while depending on the required components. |
|
Note: Clicking on the Documentation button will provide you with the default set of PDF documents which comprehensively cover most aspects of Messaging. They can also be downloaded from resources.zang.io in both PDF and HTML format. |
4.Enter the DCOM user info (domain user account which has local administrator rights). This is required by services which use local administrator rights.
Click OK after entering the necessary credentials.
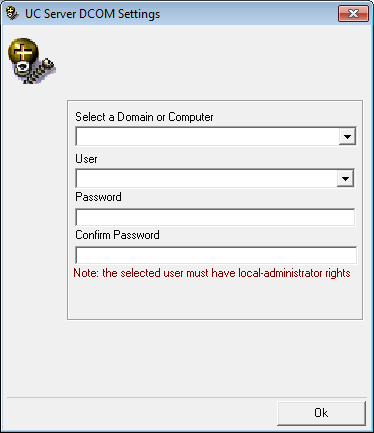
5.Review all the license agreements and select
I accept the license agreement.
Click Next to continue.
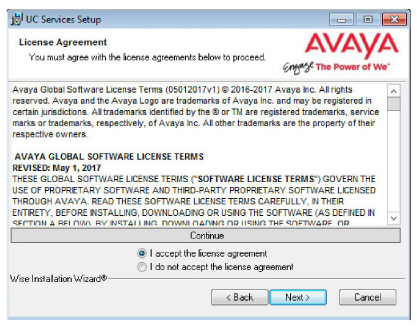
6.You will be asked to select the destination of the installation. You may change the hard drive destination through the drop down menu. By default, the installation will create a UC folder on the C drive.
Click Next to continue.
|
Note: It is highly recommended that you install the program to a drive other than C to prevent any conflicts or performance issues. |
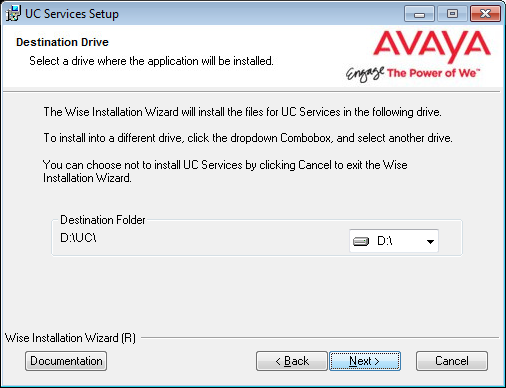
7.Enable Multiple UC Servers in High Availability.
Click Next.
Single UC Server: When operating Messaging on a single server computer.
Multiple UC Servers in High Availability: When running Messaging in High Availability mode for redundancy.
IX Messaging Cloud Gateway: Gateway allows end-to-end synchronization between the Avaya Aura Messaging server and Google's Gmail using Avaya IX Messaging message sync and the CSE. Refer to chapter 15, Install and Configure Cloud Gateway for complete details.
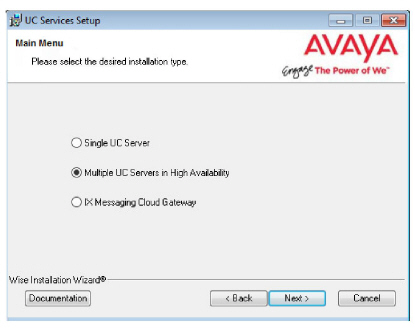
8.Select Secondary Voice Server.
Click Next.
9.Select the IP Address of the Primary Voice Server.
Click Next.
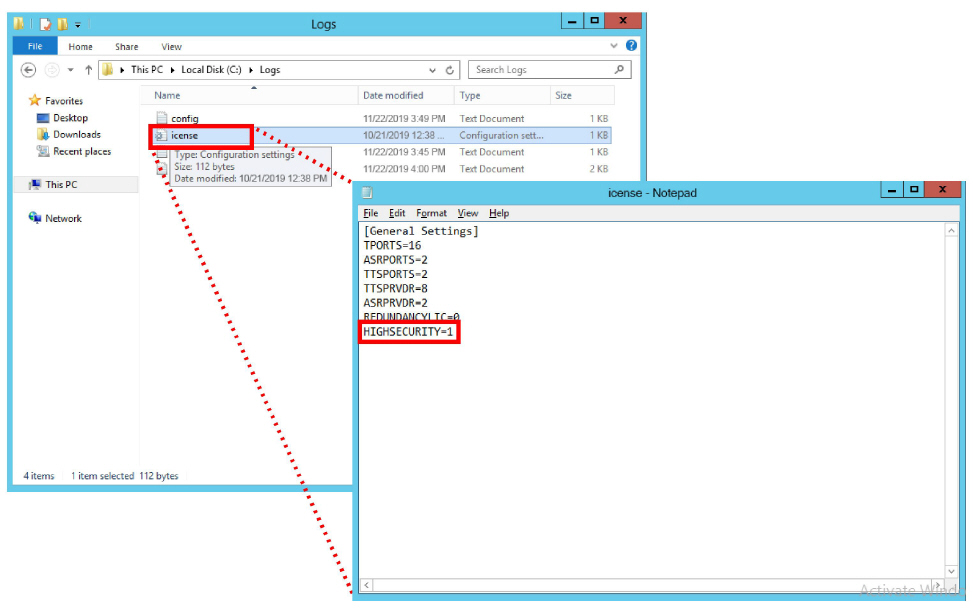
10.On the Messaging installation drive, open the Logs folder.
Open the file named license using any text editor (e.g. Notepad).
Verify Highsecurity=1. If it does not, verify that the same file (IXM Installation drive:\UC) on the Primary voice server does have this setting. If the setting is valid on the Primary, there is a connection or a sharing problem between the two machines. If the Primary is not correctly set, contact your reseller for an updated license.
Once any connection or sharing problems have been fixed, return to step 8 and check again for this file.
|
Caution: Do not continue the installation until this file has the HIGHSECURITY setting equal to 1. |
11.Select the Components required at your site.
Click Next.
12.Select your PBX Brand then click Next.

13.Select your PBX model from the dropdown menu.
Click Next.

14.Enter the number for this Secondary Server. Each Secondary must have a unique number assigned between 2 and 20.
Click Next.
15.Enter the IP Address for the Consolidated Server.
Click Next.
16.Enter the number of ports your system will use.
Click Next.
17.Create and verify a UC IIS User Password. This is used when logging into any associated web applications, such as Web Access.
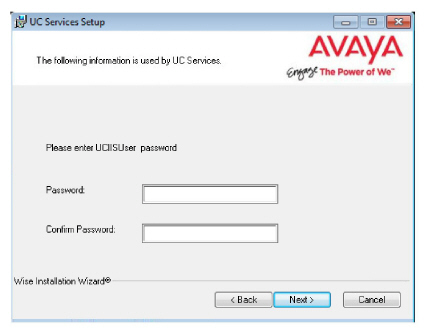
18.Enter the database encryption password. The database files will be encrypted with this password using the FIPS 140-2 certified security algorithms.
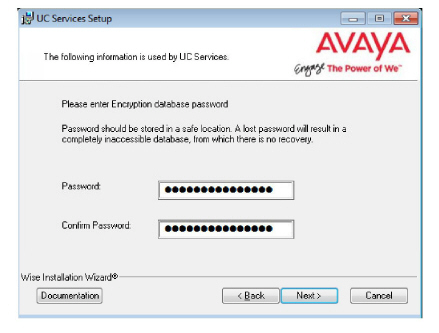

|
Important: Record this password and keep it in a safe location. |
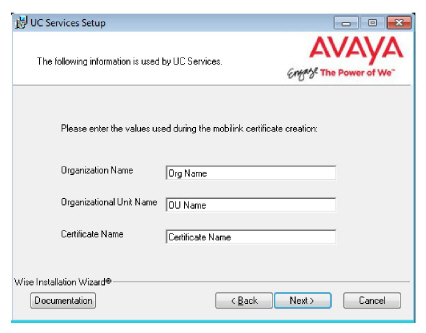
19.Enter the values in the spaces provided. These are provided with the certificate.
These values must be the same as are used during the Primary voice server installation (step 26).
20.The preliminary information required for installation is now complete.
Click Next.
21.The selected components will now be installed. This process may take a while.
22.If you are warned about components being in use, either use the automatic option or manually close the process which is interfering with the installation.
Click OK when ready.
23.After all the components are copied, you may be asked to provide the settings for the PBX that you have chosen. Since this process varies greatly from system to system, please ensure that you configure your site’s PBX exactly as required.
24.In this section of the installation wizard you will be asked to provide additional settings for SIP integration.
Click Next to continue.
25.Fill out all required information. The PBX and the Number of Channels fields are automatically populated. Enter the IP Address of the PBX.
Trunk is selected by default, and is the best option for most installations.
Select Extension if it is available through the PBX, and if Pre-Paging is required. If Extension is enabled, enter the Start Extension Number established during PBX setup.
Click Next when ready.
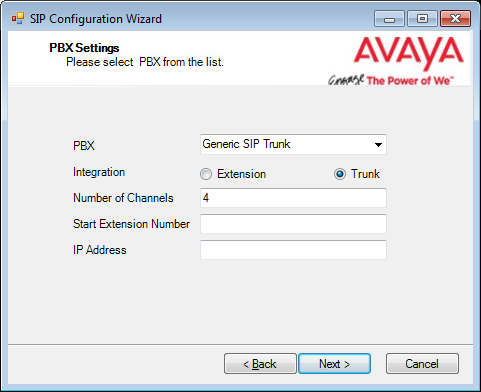
26.Confirm the information then click Finish.
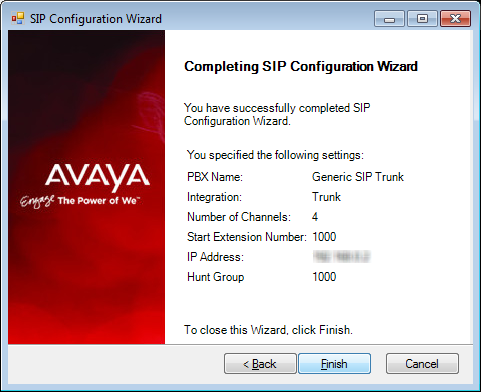
|
Note: Depending on the type of SIP integration you’ll be using, you may have to fine tune the settings from the SIP Configuration Tool in order for the system to function properly. The SIP Configuration Tool can be found in the Messaging programs folder after installation. |
27.Click Finish to restart the server.
If you wish to restart your computer at a later time, disable the Restart check box then click Finish.
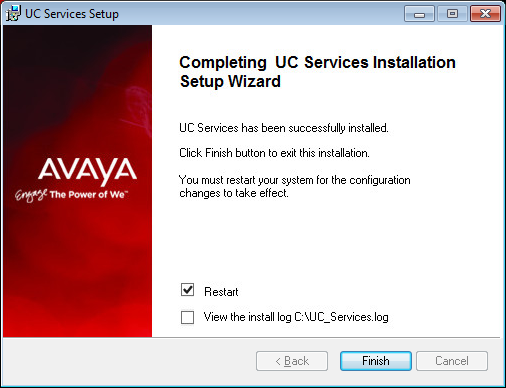
28.This alert is to remind you to properly share the UC installation folder (see here for details).

|
Important: The installation folder MUST be shared before proceeding with the Consolidated and Secondary server installations. |
29.Verify that the Encryption File System (EFS) certificate has been saved to another secure location (see Backup and Restore the Certificate File on page 287). If the certificate becomes corrupted, UC Communication will no longer function and are unrecoverable without this backup file.
Click OK to restart the computer.
More stringent rules for user passwords are also required for a JITC certified installation. These include:
•Passwords must be at least 15 characters long.
•It must include at least one uppercase character (A-Z).
•...include at least one lowercase character (a-z).
•...include at least one non-alphabetic character (0-9, !@#$% etc.).
•A password must be changed every 60 days.
•No new password can be the same as a previous password extending back 10 iterations.
•The administrator can change the password at any time.
•The client can change their password only once within a 24 hour period.
•A client password can only be changed by the client or the administrator.
•A password cannot contain any personal information, such as names, telephone numbers, birthdays, etc.
These rules are enabled by automatically when installing the JITC compliant edition of Avaya IX Messaging. They can also be manually enabled through the IXM Admin MMC under Configuration > Advanced.
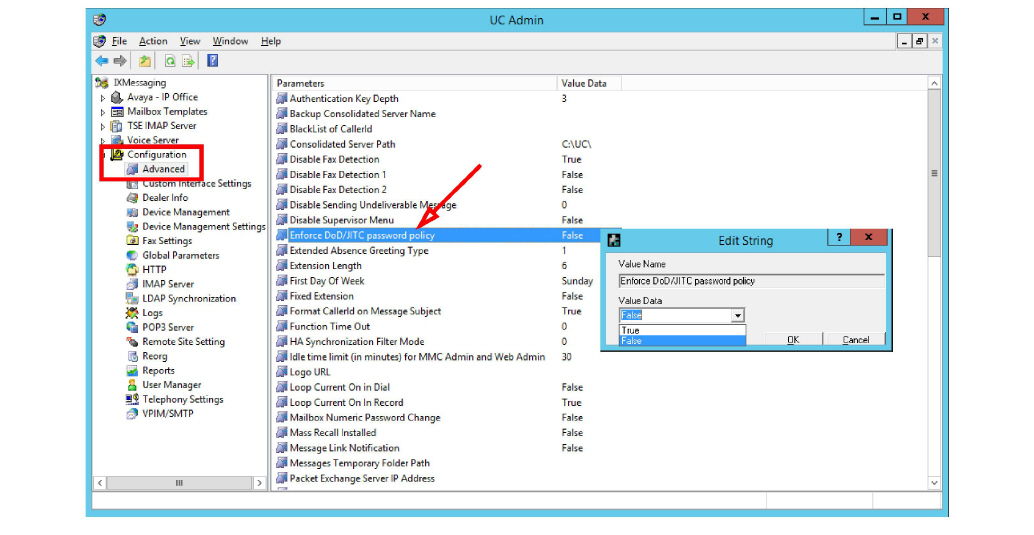
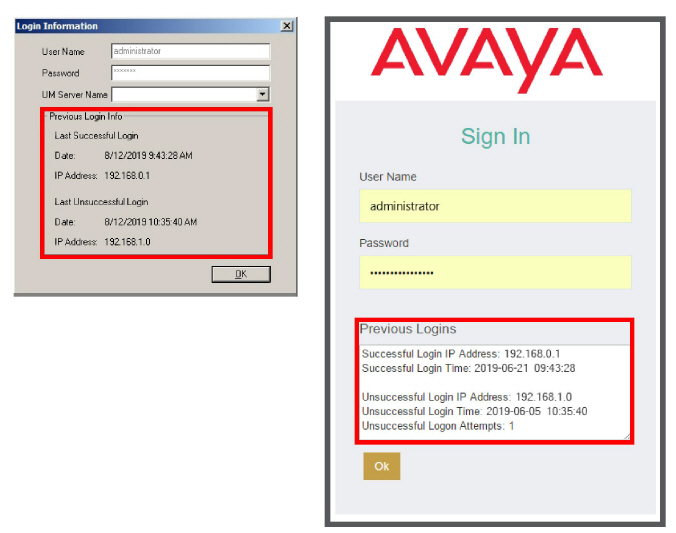
When logging in to Avaya IX Messaging applications (i.e. IXM Admin, Web Admin), after putting in a correct password, the user is shown the details for the last successful and unsuccessful login attempts through their account. The details include the date and time of the attempt and the IP address of the machine where the attempt was launched.
Review the details as necessary, then click OK to complete the login process and launch the application.
Creating Public and Private Keys
Use the included utility to generate the required public and private keys used by Mobilink services to encrypt data in the synchronization process.
1.On the Primary computer, open the drive where Avaya IX Messaging has been installed.
Open the Sybase\SQL Anywhere 17\BIN64 folder and run the createkey program.
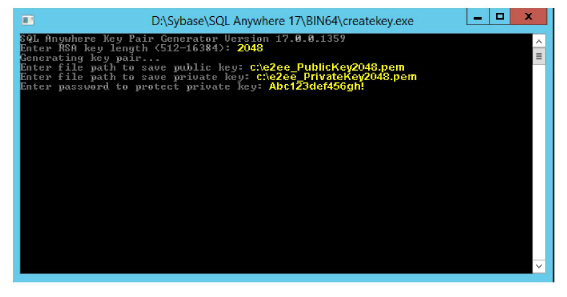
2.At the prompt, enter 2048, then press Enter.
3.Key in the location where you want the public key to be stored. Include the name of the key.
The name MUST be e2ee_PublicKey2048.pem . Press Enter.
4.Key in the location where you want the private key to be stored. Include the name of the key.
The name MUST be e2ee_PrivateKey2048.pem . Press Enter.
5.Enter a password for Mobilink end-to-end encryption and press Enter. The password is the same as the one entered during the Consolidated server installation step 19.
6.Copy the file generated for the public key to the Primary voice server, and to all Secondary servers.
Paste the file into the UC\Certificates folder on the drive where Avaya IX Messaging was installed.
Copy the file generated for the private key to the same folder on the Consolidated server.
Certificates for Mobilink Connection: Self-Signed
|
Hint: If your site does not permit self-signed certificates, use the Certificates for Mobilink Connection: Not Self-Signed section on here instead. Only one of these procedures is required. |
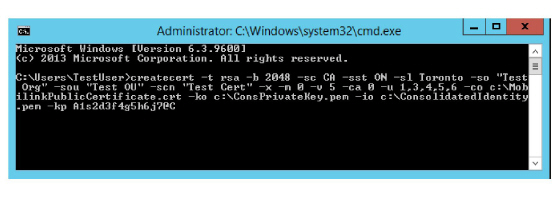
If you are using a self-signed certificate, run the following script from the command prompt to generate the Consolidated server identity and public certificates used by Mobilink services for authentication.
Change the highlighted sections so that they apply to your installation. Enter the same values that were used during the installation of the Primary voice server (step 26 on here).
Enter the password you chose for the Consolidated server during installation (Abc123def456gh! in this example).
All passwords must be JITC compliant (see here).
createcert -t rsa -b 2048 -sc CA -sst ON -sl Toronto -so "Test Org" -sou "Test OU" -scn "Test Cert" -x -m 0 -v 5 -ca 0 -u 1,3,4,5,6 -co c:\MobilinkPublicCertificate.crt -ko c:\ConsPrivateKey.pem -io c:\ConsolidatedIdentity.pem -kp Abc123def456gh!
Copy the ConsolidatedIdentity.pem certificate file to the UC\Certificates folder on the Consolidated server to the drive where Avaya IX Messaging was installed.
For a certificate provided by a CA, rename the private key file and copy here. The self-signed certificate created in step will already have this name.
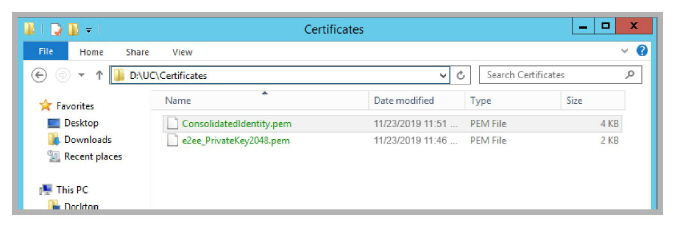
Copy the MobilinkPublicCertificate.crt certificate file to the UC\Certificates folder on the Primary and all Secondary servers to the drive where Avaya IX Messaging was installed.
For a certificate provided by a CA, rename the public key file and copy here. The self-signed certificate created in step will already have this name.
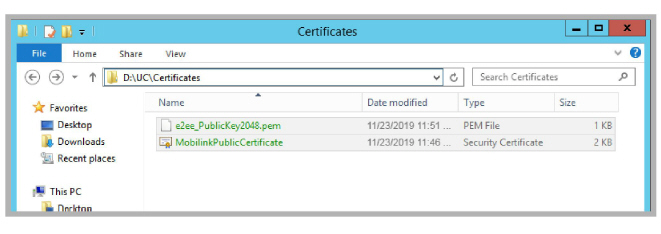
Certificates for Mobilink Connection: Not Self-Signed
|
Hint: If self-signed certificates are satisfactory, use the Certificates for Mobilink Connection: Self-Signed section on here instead. Only one of these procedures is required. |
If your site does not permit self-signed certificates, run the following scripts from the command prompt to generate the Consolidated server identity and public certificates used by Mobilink services for authentication.
Change the highlighted sections so that they apply to your installation. Enter the same values that were used during the installation of the Primary voice server (step 26 on here).
Enter the password you chose for the Consolidated server during installation (Abc123def456gh! in this example).
The Private certificate password (Zyx987wvu654ts! in this example) is created here and must appear in the Public certificate command line.
All passwords must be JITC compliant (see here).
•Private Certificate: This certificate will reside on the Consolidated server.
createcert -t rsa -b 2048 -sc CA -sst ON -sl Toronto -so "Test Org" -sou "Test OU" -scn "Test Cert" -x -m 0 -v 5 -ca 1 -u 6,7 -co c:\MobilinkPublicCertificateCA.pem -ko c:\ConsPrivateKeyCA.pem -io c:\ConsolidatedIdentityCA.pem -kp "Zyx987wvu654ts!"
•Public Certificate: This certificate is used by Avaya IX Messaging to validate access using the private certificate. Copies must be made on the Primary and all Secondary voice servers.
createcert -t rsa -b 2048 -sc CA -sst ON -sl Toronto -so "Test Org" -sou "Test OU" -scn "Test Cert" -m 0 -v 5 -ca 0 -u 1,3,4,5,6 -c c:\MobilinkPublicCertificateCA.pem -ck c:\ConsPrivateKeyCA.pem -cp "Zyx987wvu654ts!" -co c:\MobilinkPublicCertificate.crt -ko c:\ConsPrivateKey.pem -io c:\ConsolidatedIdentity.pem -kp "Abc123def456gh!"

The certificate files are created in the root directory of the C:\ drive.
Copy the ConsolidatedIdentity.pem certificate file to the UC\Certificates folder on the Consolidated server drive where Avaya IX Messaging was installed.

Copy the MobilinkPublicCertificate.crt certificate file to the UC\Certificates folder on the Primary and all Secondary servers to the drive where Avaya IX Messaging was installed.
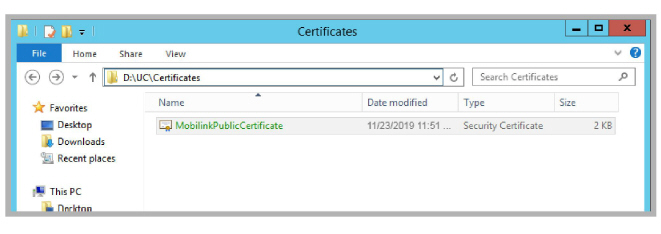
Configuring TLS with Messaging for SIP
After Avaya IX Messaging has been installed, modifications must be made to the ETSIPService.ini file. This will enable TLS security with the correct settings for use with Messaging.
The ETSIPService.ini file is located in the UC/Configuration folder on the voice server hard drive.
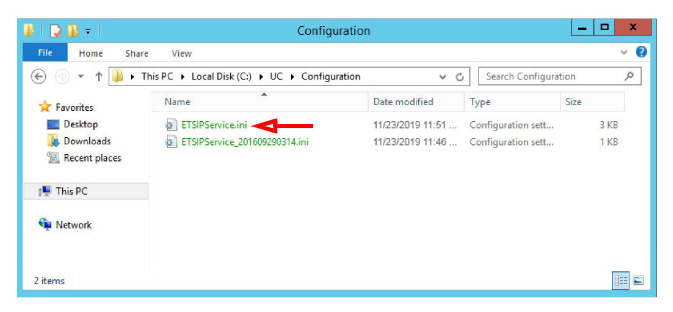
Open it using Notepad or any similar text editor.
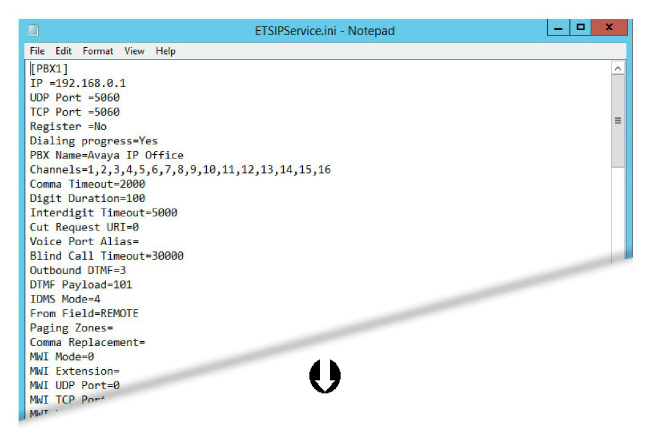
Make the necessary changes to the data in the file. If an item is not present, add it to the appropriate section. Create a new section at the end of the file if necessary.
This is an example of additions and changes that can be made to the file. Make the changes required for your site.
[PBX1]
Transport protocol=3
Enforce Secure RTP=1
MWI TCP Port = 5061
TCP Port = 5061
[SIP settings]
Ignore Local Addresses=Yes
TCP Enabled = Yes
TLS IP = 192.168.0.1:5061
[TLS Manager]
FIPS=0
[TLS Server]
Private [email protected]
Certificate Depth=5
Method=2
[TLS Client]
Intermediate [email protected]
Certificate Depth=5
Method=2
Key
Transport protocol: Set this value to 3. A TLS IP address must be defined under SIP settings.
Enforce Secure RTP: Enter 1 to allow both AVP and SAVP. Setting this to 2 will use secure RTP.
MWI TCP Port / TCP Port: Set both of these values to 5061.
Ignore Local Addresses: Allows control of automatic stack binding with all available interfaces. This must be set to Yes when using TLS.
TCP Enabled: TCP is required for use with TLS. Set this option to Yes.
TLS IP: List all of the TLS local IP addresses for the Messaging server. The format must be address, colon, port. For example, IPAddress:port . Separate multiple server addresses in the list using a comma.
FIPS: Enables the FIPS module for an OpenSSL library.
Private Key: Enter the full path to the private key file (i.e. c:\security\certificates\sip.key). Adding the prefix @ will automatically include the path to the Messaging certificates folder: entering @sip.key expands the path to C:\UC\Certificates\sip.key (where C is the drive where Messaging is installed). The certificate file must be in PEM format.
Certificate: Enter the full path to the certificate file (i.e. c:\security\certificates\sip.crt). Adding the prefix @ will automatically include the path to the Messaging certificates folder: entering @sip.crt expands the path to C:\UC\Certificates\sip.crt (where C is the drive where Messaging is installed).
Certificate Depth: Defines the depth that an engine will consider legal in a certificate chain (certificates authorizing certificates). The default value is 5.
Method: Specify the version of TLS to use. The default value is 2 (TLS 1.2). If you installation requires an earlier version of TLS, change the value accordingly.
|
Value |
Version |
|---|---|
|
4 |
TLS 1.0 |
|
3 |
TLS 1.1 |
|
2 |
TLS 1.2 |
|
1 |
SSL 3.1 |
CA Certificates: Enter the full path to the PEM certificate file. Adding the prefix @ will automatically include the path to the Messaging certificates folder. A TLS engine can trust zero, one or more root certificates. Once an engine trusts a root certificate, it will approve all valid certificates issued by that root certificate.
Intermediate Certificates: Enter the full path to the PEM certificate file. Adding the prefix @ will automatically include the path to the Messaging certificates folder. An engine may hold a certificate that is not issued directly by a root certificate, but by a certificate authority delegated by that root certificate. To add this intermediate certificate to the chain of certificates that the engine will present during a handshake.
Certificate Depth: Defines the depth that an engine will consider legal in a certificate chain (certificates authorizing certificates). The default value is 5.
Method: Specify the version of TLS to use. The default value is 2 (TLS 1.2). If your installation requires an earlier version of TLS, change the value accordingly.
|
Value |
Version |
|---|---|
|
4 |
TLS 1.0 |
|
3 |
TLS 1.1 |
|
2 |
TLS 1.2 |
|
1 |
SSL 3.1 |
|
Note: Some sites may require Mutual Certification between the Messaging voice server and the PBX. To configure this item, copy the Private Key and Certificate elements from TLS Server into the TLS Client section. [TLS Client] |
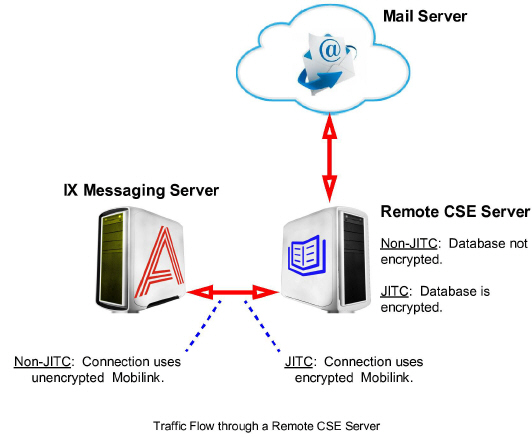
Installing Remote CSE Under JITC
When adding a Remote CSE server as part of a High Availability JITC installation, extra steps must be taken. JITC uses encryption to secure data and communications between devices, so this extra layer must be incorporated into the configuration to ensure compliance.
The communications channel between the CSE Server and the Messaging Servers must be encrypted in a JITC compliant installation. Similarly, the database on the CSE server must also be encrypted for data storage.
|
Important: The presence of a JITC license will be noted by the Wizard during installation and the appropriate files will be loaded. Encryption will be automatically enabled at that time. |
|
Note: Each Remote CSE Server supports a single email type (e.g. Exchange, Office 365, Gmail, etc.). If more than one email type is required, the Consolidated Server cannot be used for synchonization. |
1.On the computer designated as the Remote CSE Server, open the Avaya IX Messaging folder on your server hard drive and run Setup.exe as administrator to launch the installer.
When prompted, click Next.
2.Enter the DCOM user info (domain user account which has local administrator rights). This is required by services which use local administrator rights.
Click OK after entering the credentials.

3.Review the license agreement. Click Continue, enable the I accept the license agreement checkbox, then click Next.
4.You will be asked to select the destination directory for the installation. You may change the hard drive destination through the drop down menu. By default, the installation will create a UC folder on the C drive.
Click Next to continue.
|
Note: It is highly recommended that you install the program to a drive other than C to prevent any conflicts or performance issues. |

5.Enable Multiple UC Servers in High Availability.
Click Next.
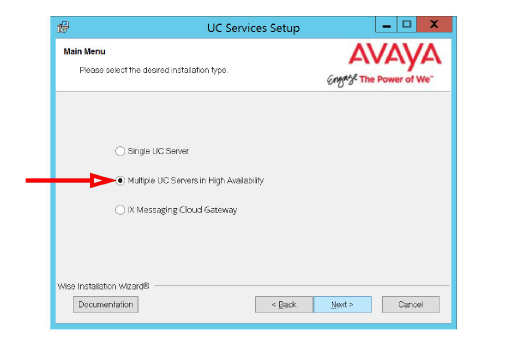
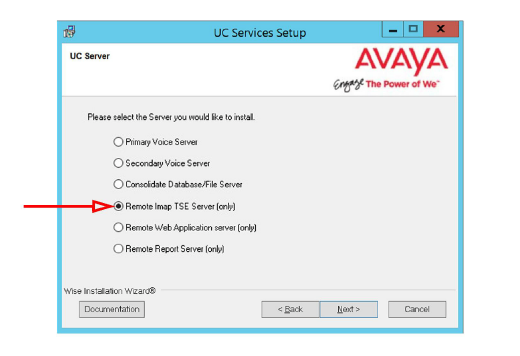
6.Select Remote Imap TSE Server (only).
Click Next.
7.Enter a number between 1-25 for this server.
If you configure multiple CSE servers, each must be given a unique number; no two servers can share the same number.
Avaya IX Messaging supports up to 25 CSE servers.
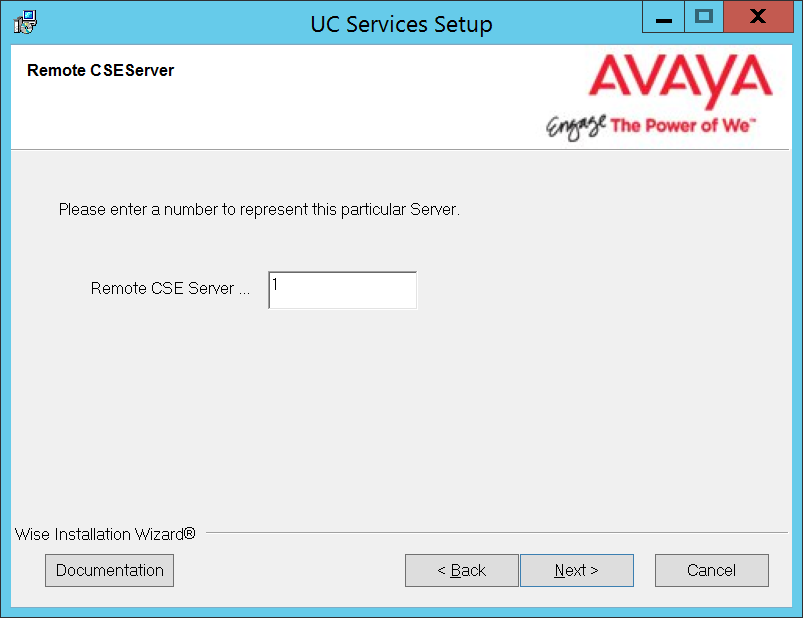
Click Next.
|
Note: Each CSE server can support up to 5000 users. |
8.Enter the IP Address of the Primary server.
Click Next.
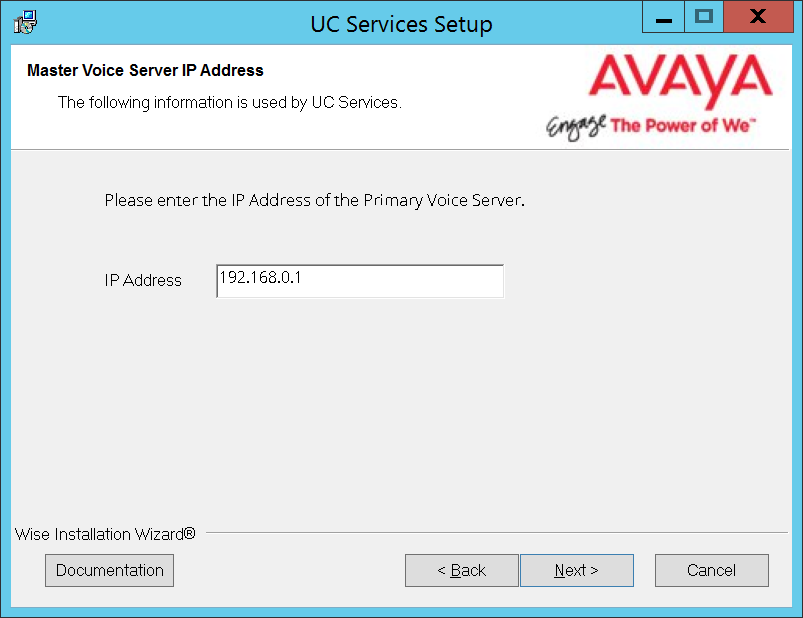
9.On the C drive, open the Logs folder.
Open the file named license using any text editor (e.g. Notepad).
Verify Highsecurity=1. If it does not, verify that the same file (IXM Installation drive:\UC) on the Primary voice server does have this setting. If the setting is valid on the Primary, there is a connection or a sharing problem between the two machines. If the Primary is not correctly set, contact your reseller for an updated license.
Once any connection or sharing problems have been fixed, return to step 9 and check again for this file.
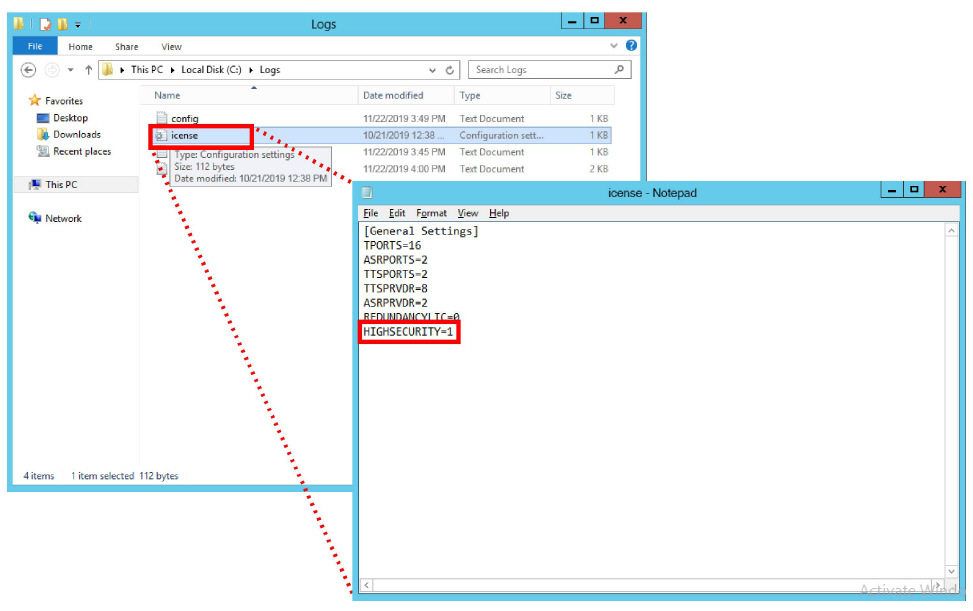
|
Caution: Do not continue the installation until this file has the Highsecurity setting equal to 1. |
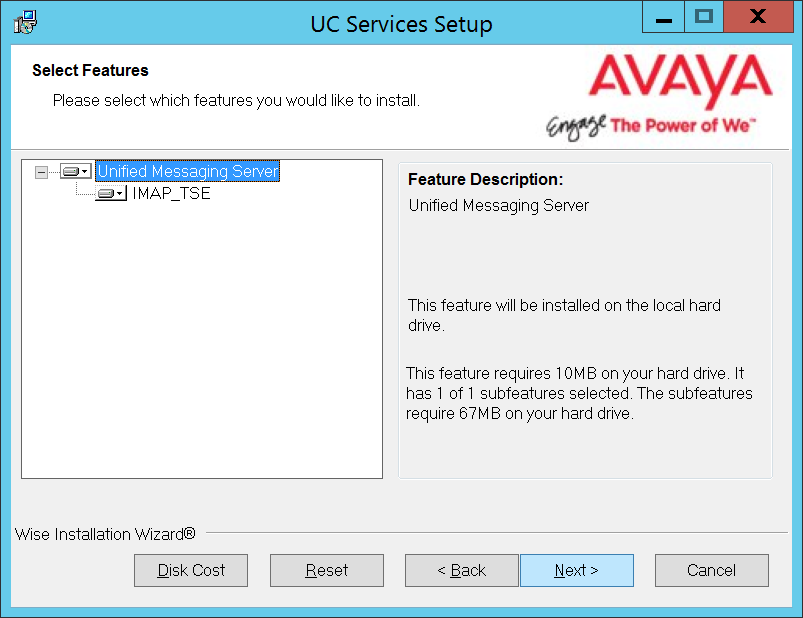
10.Select the Components required at your site. Disable any components that are not needed.
Click Next.
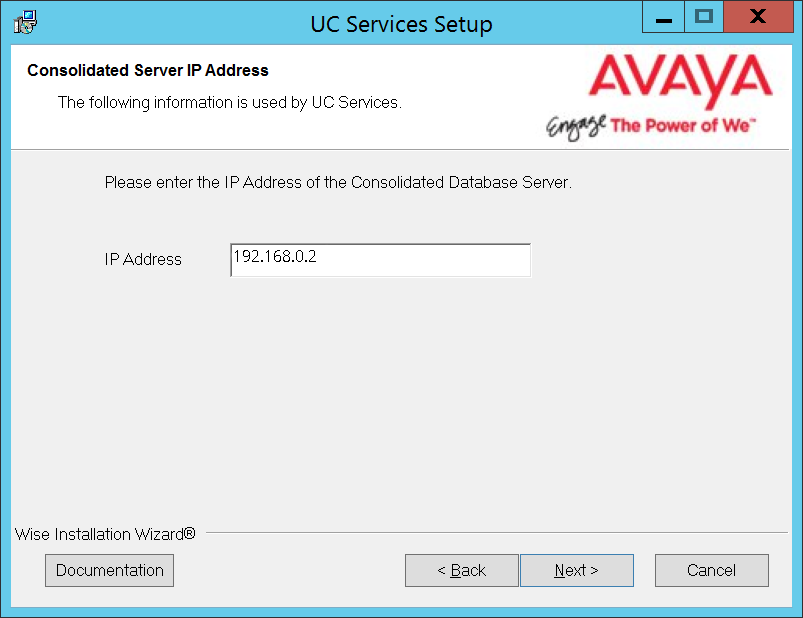
11.Enter the IP Address for the Consolidated server.
Click Next.
12.Select the Email Server Type from the list of available options. This allows the system to set basic parameters which help to improve performance and reliability.
When ready, click Next.

|
Note: Each Remote CSE Server supports a single email type (e.g. Exchange, Office 365, Gmail, etc.). If more than one email type is required, the Consolidated Server cannot be used for synchonization. |
13.Enter the database encryption password. The database files will be encrypted with this password using the FIPS 140-2 certified security algorithms.
This password must meet the requirements outlined here.
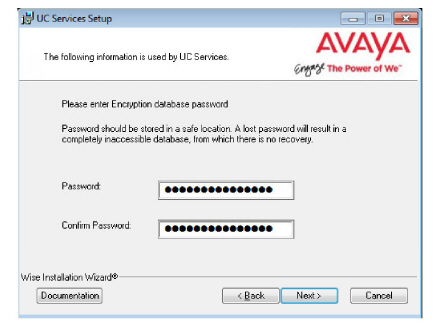
|
Important: Record this password and keep it in a safe location. |
14.Enter the values in the spaces provided. These are provided with the certificate.
These values must be the same as are used during the Primary voice server installation (step 26).
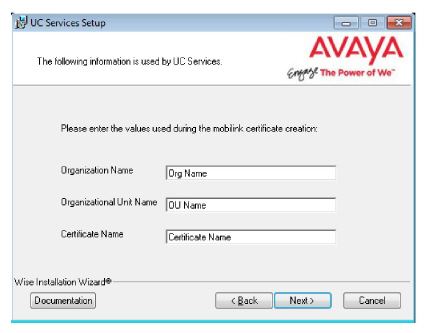
15.The preliminary information required for installation is now complete.
Click Next.
16.The selected components will now be installed. This process may take a while.
17.Click Finish to restart the server.
If you wish to restart your computer at a later time, disable the Restart check box, then click Finish.
18.This alert is to remind you to properly share the UC installation folder (see here for details).

|
Important: The installation folder MUST be shared before proceeding with the Consolidated and Secondary server installations. |
19.Verify that the Encryption File System (EFS) certificate has been saved to another secure location (see Backup and Restore the Certificate File on page 287). If the certificate becomes corrupted, UC Communication will no longer function and are unrecoverable without this backup file.
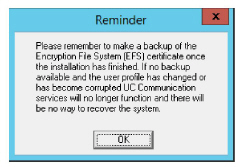
Click OK to restart the computer.
The Remote CSE server installation is complete.
Installing Remote Web Server Under JITC
When adding a Remote Web server as part of a High Availability JITC installation, extra steps must be taken. JITC uses encryption to secure data and communications between devices, so this extra layer must be incorporated into the configuration to ensure compliance.
The communications channel between the Web Server and the Messaging Servers must be encrypted in a JITC compliant installation. Similarly, the database on the Web server must also be encrypted for data storage.
|
Important: The presence of a JITC license will be noted by the Wizard during installation and the appropriate files will be loaded. Encryption will be automatically enabled at that time. |
1.On the computer designated as the Remote Web Server, open the Avaya IX Messaging folder on your server hard drive and run Setup.exe as administrator to launch the installer.
When prompted, click Next.
2.Enter the DCOM user info (domain user account which has local administrator rights). This is required by services which use local administrator rights.
Click OK after entering the credentials.

3.Review the license agreement. Click Continue, enable the I accept the license agreement checkbox, then click Next.
4.You will be asked to select the destination directory for the installation. You may change the hard drive destination through the drop down menu. By default, the installation will create a UC folder on the C drive.
Click Next to continue.
|
Note: It is highly recommended that you install the program to a drive other than C to prevent any conflicts or performance issues. |
5.Enable Multiple UC Servers in High Availability.
Click Next.
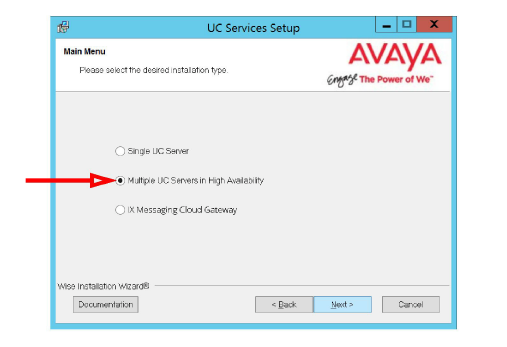
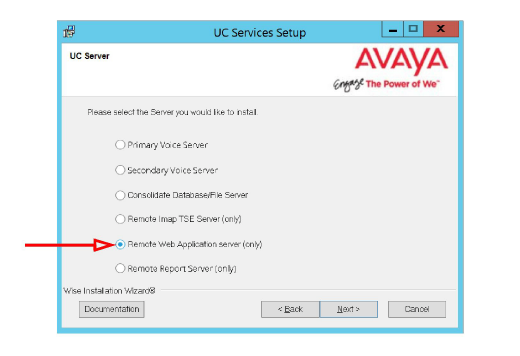
6.Select Remote Web Application server (only).
Click Next.
7.Enter a number between 1-14 for this server.
If you configure multiple Web servers, each must be given a unique number; no two servers can share the same number.
Avaya IX Messaging supports up to 14 Web servers.
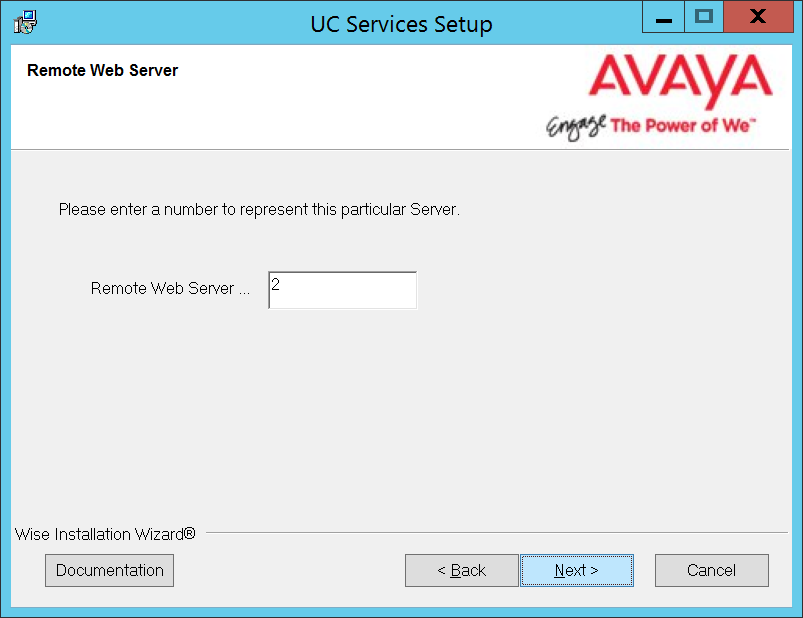
Click Next.
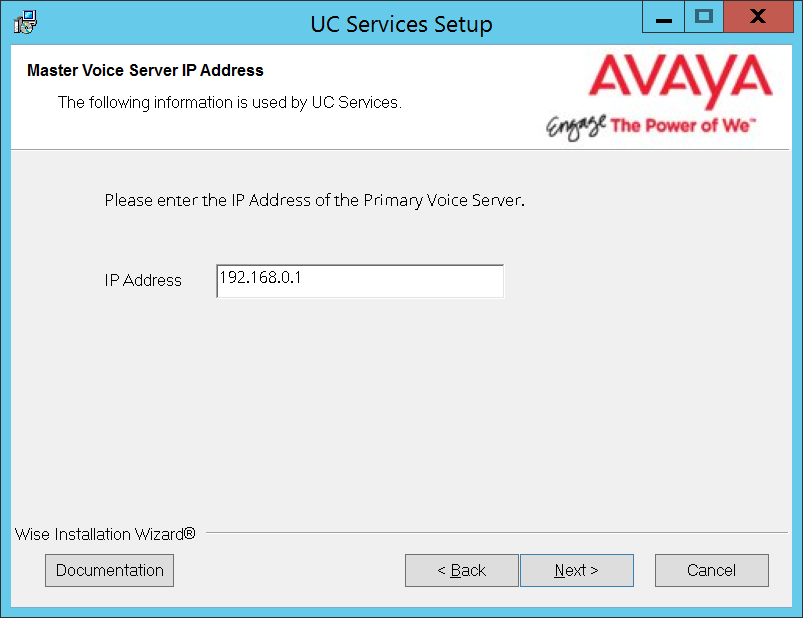
8.Enter the IP Address of the Primary server.
Click Next.
9.On the C drive, open the Logs folder.
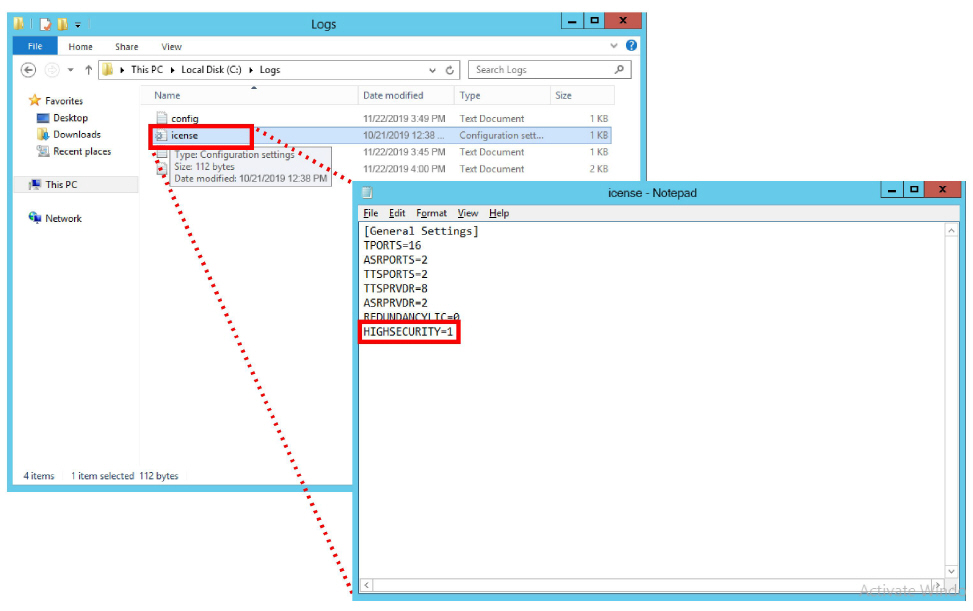
Open the file named icense using any text editor (e.g. Notepad).
Verify Highsecurity=1. If it does not, verify that the same file (IXM Installation drive:\UC) on the Primary voice server does have this setting. If the setting is valid on the Primary, there is a connection or a sharing problem between the two machines. If the Primary is not correctly set, contact your reseller for an updated license.
Once any connection or sharing problems have been fixed, return to step 9 and check again for this file.
|
Caution: Do not continue the installation until this file has the Highsecurity setting equal to 1. |
10.Select the Components required at your site. Disable any components that are not needed.
Click Next.
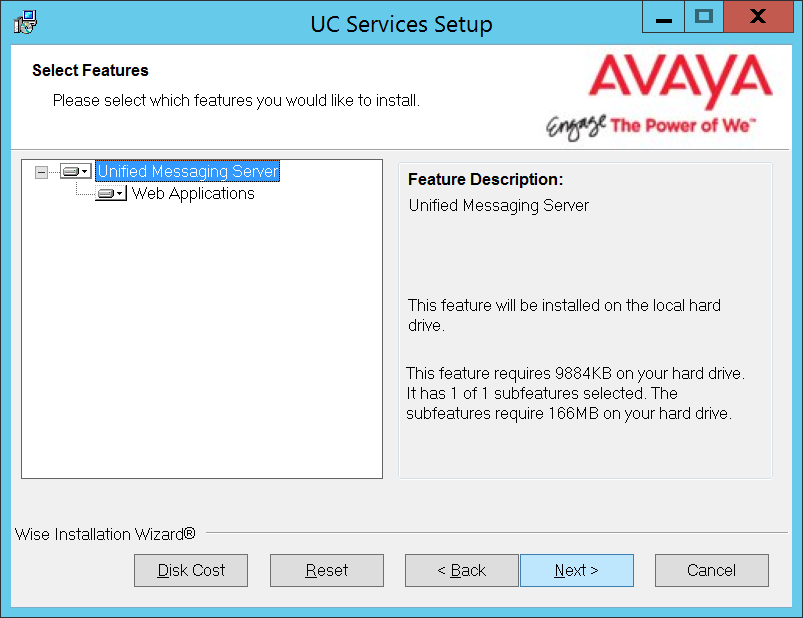
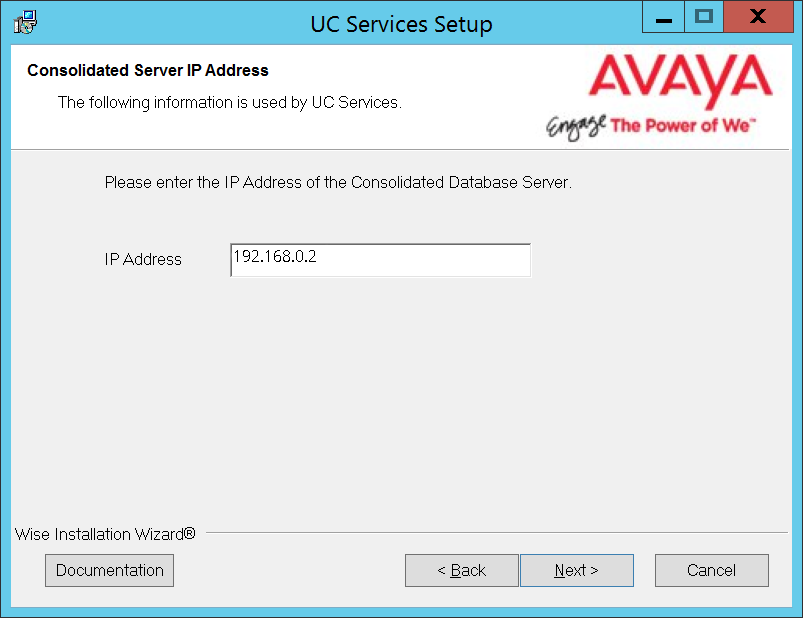
11.Enter the IP Address for the Consolidated server.
Click Next.
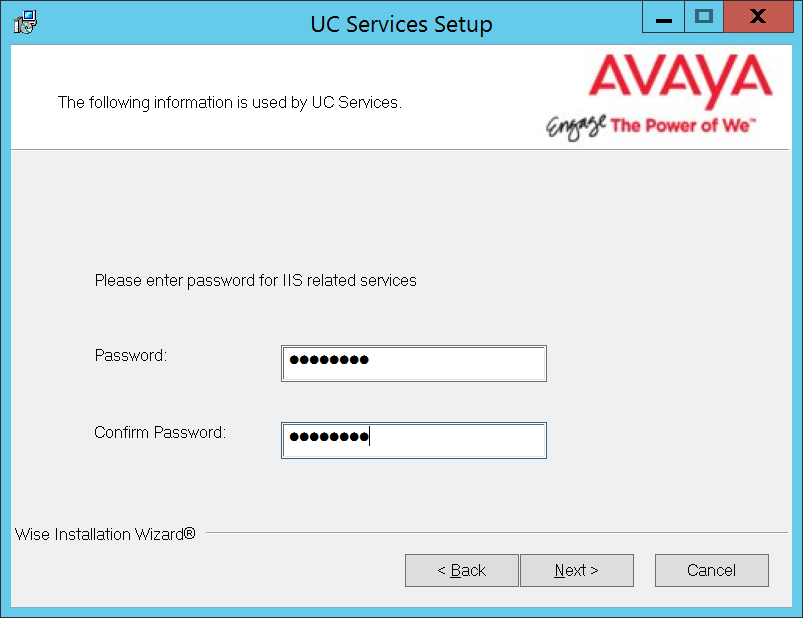
12.Enter and confirm the password for the UCIIS user. This must be the same UCIIS password that was created on the other servers.
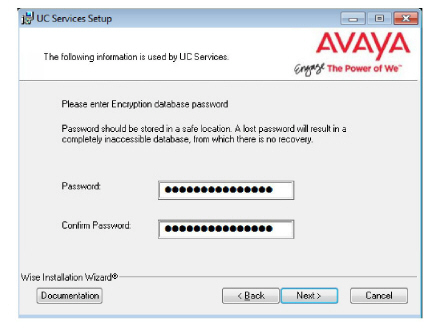
13.Enter the database encryption password. The database files will be encrypted with this password using the FIPS 140-2 certified security algorithms.
This password must meet the requirements outlined here.
|
Important: Record this password and keep it in a safe location. |
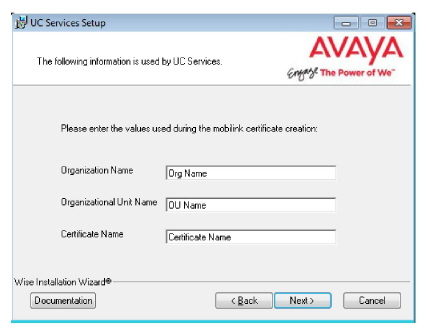
14.Enter the values in the spaces provided. These are provided with the certificate.
These values must be the same as are used during the Primary voice server installation.
15.The preliminary information required for installation is now complete.
Click Next.
16.The selected components will now be installed. This process may take a while.
17.Click Finish to restart the server.
If you wish to restart your computer at a later time, disable the Restart check box, then click Finish.
18.This alert is to remind you to properly share the UC installation folder (see here for details).

|
Important: The installation folder MUST be shared before proceeding with the Consolidated and Secondary server installations. |
19.Verify that the Encryption File System (EFS) certificate has been saved to another secure location (see Backup and Restore the Certificate File on page 287). If the certificate becomes corrupted, UC Communication will no longer function and are unrecoverable without this backup file.
Click OK to restart the computer.
The Remote Web server installation is complete.